AppleInsider could earn an affiliate fee on purchases made via hyperlinks on our web site.
Apple is not checking photos seen inside the macOS Finder for CSAM content material, an investigation into macOS Ventura has decided, with evaluation indicating that Visible Lookup is not being utilized by Apple for that individual goal.
In December, Apple introduced it had given up on plans to scan iPhone photographs uploaded to iCloud for Little one Sexual Abuse Materials (CSAM), following appreciable backlash from critics. Nonetheless, rumors apparently lingered alleging that Apple was nonetheless performing checks in macOS Ventura 13.1, prompting an investigation from a developer.
In line with Howard Oakley of Electrical Mild Co. in a blog post from January 18, a declare began to flow into that Apple was mechanically sending “identifiers of photos” {that a} consumer had browsed in Finder, doing so “with out that consumer’s consent or consciousness.”
The plan for CSAM scanning would’ve concerned a neighborhood on-device verify of photos for potential CSAM content material, utilizing a hashing system. The hash of the picture would then be despatched off and checked towards a listing of recognized CSAM recordsdata.
Whereas the concept of scanning photos and making a neural hash to be despatched off to Apple to explain traits of picture may feasibly be used for CSAM scanning, Oakley’s testing signifies it isn’t actively being utilized in that method. As an alternative, it appears that evidently Apple’s Visual Lookup system, which permits macOS and iOS to determine folks and objects in a picture, in addition to textual content, might be mistaken for conducting on this type of conduct.
No proof in checks
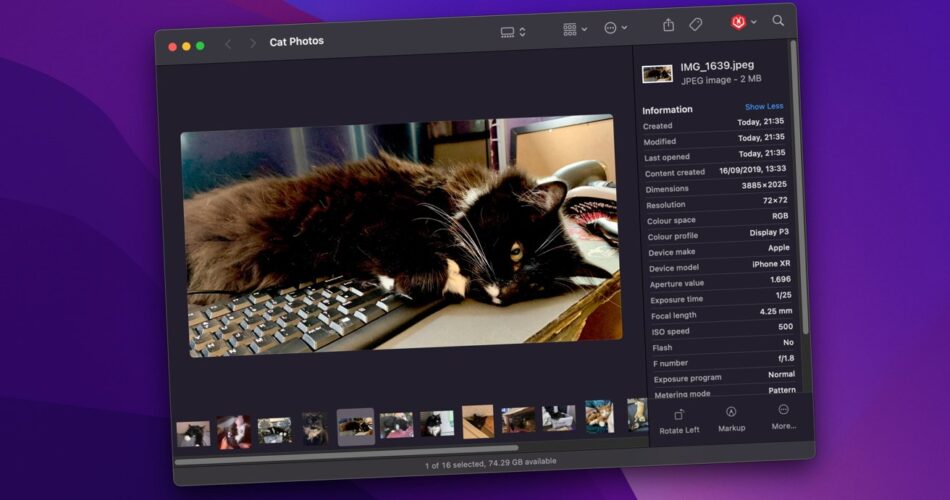
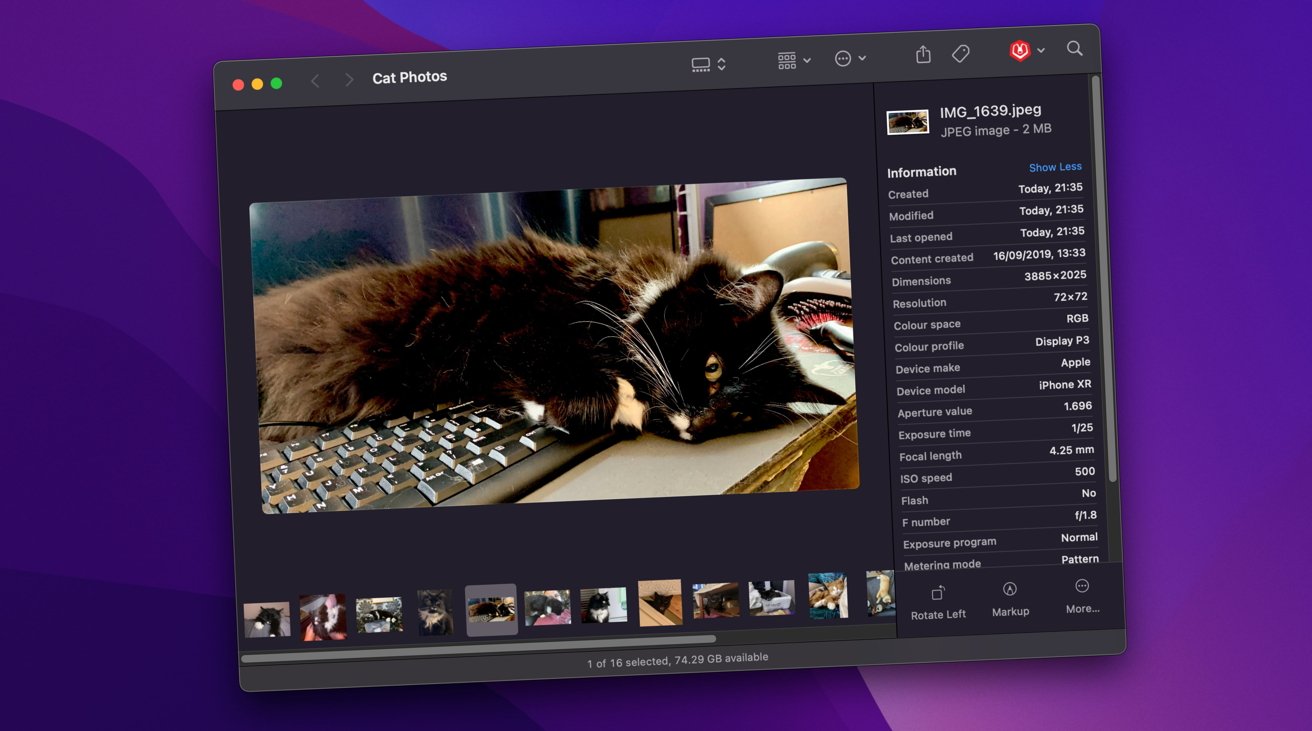
As a part of testing, macOS 13.1 was run inside a digital machine and the appliance Mints was used to scan a unified log of actions on the VM occasion. On the VM, a set of photos have been seen for a interval of 1 minute in Finder’s gallery view, with greater than 40,000 log entries captured and saved.
If the system was used for CSAM evaluation, there could be repeated outgoing connections from the “mediaanalysisd” to an Apple server for every picture. The mediaanalysisisd refers to a component utilized in Visible Lookup the place Photographs and different instruments can show details about detected gadgets in a picture, similar to “cat” or the names of objects.
The logs as a substitute confirmed that there have been no entries related to mediaanalysisd in any respect. An additional log extract was then discovered to be similar to Visible Lookup because it appeared in macOS 12.3, in that the system hasn’t materially modified since that launch.
Usually, mediaanalysisd would not contact Apple’s servers till very late within the course of itself, because it requires neural hashes generated by picture evaluation beforehand. As soon as despatched off and a response is acquired again from Apple’s servers, the acquired knowledge is then used to determine to the consumer components inside the picture.
Additional trials decided that there have been another makes an attempt to ship off knowledge for evaluation, however for enabling Reside Textual content to operate.
In his conclusion, Oakley writes that there’s “no proof that native photos on a Mac have identifiers computed and uploaded to Apple’s servers when seen in Finder home windows.”
Whereas photos seen in apps with Visible Lookup assist have neural hashes produced, which might be despatched to Apple’s servers for evaluation. Besides that making an attempt to reap the neural hashes for detecting CSAM “could be doomed to failure for a lot of causes.”
Native photos in QuickLook Preview additionally go beneath regular evaluation for Reside Textual content, however “that does not generate identifiers that might be uploaded to Apple’s servers.”
Moreover, Visible Lookup might be disabled by turning off Siri Recommendations. Exterior mediaanalysiss look-ups may be blocked utilizing a software program firewall configured to dam port 443, although “that will nicely disable different macOS options.”
Oakley concludes the article with a warning that “alleging {that a} consumer’s actions end in controversial results requires full demonstration of the complete chain of causation. Basing claims on the inference that two occasions is perhaps linked, with out understanding the character of both, is reckless if not malicious.”
CSAM nonetheless a difficulty
Whereas Apple has gone off the concept of performing native CSAM detection processing, lawmakers nonetheless imagine Apple is not doing sufficient about the issue.
In December, the Australian e-Security Commissioner attacked Apple and Google over a “clearly insufficient and inconsistent use of extensively out there know-how to detect baby abuse materials and grooming.”
Relatively than straight scanning for current content material, which might be largely ineffective as a consequence of Apple utilizing absolutely end-to-end encrypted photograph storage and backups, Apple as a substitute appears to need to go down a special method. Particularly, one that may detect nudity included in photographs despatched over iMessage.

Source link