The collapse of Silicon Valley Financial institution (SVB) late final week despatched tremors by the worldwide monetary system, creating alternatives for short-sellers … and quite a few species of scammer.
In accordance with numerous researchers and safety corporations, risk actors are already out attempting to find SVB-exposed prey by each passive and energetic phishing scams, together with related pretend domains and enterprise e-mail compromise (BEC) assaults.
Dean of Analysis at SANS Know-how Institute, Johannes Ullrich clocked a fast improve within the variety of area registrations containing the phrase “SVB” because the March tenth collapse.
“Over the weekend, we noticed various area registrations monitoring the Silicon Valley Financial institution failure (e.g. svblogin.com, loginsvg.com and such),” he wrote on LinkedIn.
“We additionally obtained stories that former SVB prospects are sending easy emails to replace their distributors with new ACH account info. Please cease that. Only a matter of time for the dangerous guys to spoof emails like that (if they do not already do it).”
Ullrich additionally noted that SVB’s failure has some engaging options for rip-off operators: cash, urgency and uncertainty.
“For a lot of, it is not clear learn how to talk with SVB, what web site to make use of, or what emails to anticipate (or the place they may come from?)” wrote Ullrich.
Ullrich isn’t the one one noticing a rise in SVB-referencing area registrations.
New area registrations regarding Silicon Valley Financial institution are rising. Some may very well be #phishing campaigns. Listed beneath is what we’re seeing now. Remember not all are scammy, and never all scammy domains focusing on SVB could have SVB-related phrases: https://t.co/mHjfZQIQAf pic.twitter.com/Au7AbA0GhX
— SecuritySnacks (@SecuritySnacks) March 13, 2023
The infrastructure leveraging the domains have additionally began to look.
Count on completely different risk actors to take advantage of the present scenario with SVB. Began to see some infrastructure being setup that may very well be used for phishing / scams. login-svb[.]com cash4svb[.]com svbclaim[.]com svbdebt[.]com pic.twitter.com/rn9ltBsxDU
— Jaime Blasco (@jaimeblascob) March 12, 2023
Cloudflare mentioned on Tuesday it had detected a big Know-Your-Buyer (KYC) phishing marketing campaign that leaned on SVB branding in a DocuSign themed template. The net safety agency mentioned that inside hours of the marketing campaign, it had detected its use 79 occasions.
An assault despatched to the corporate’s CEO included HTML code with an preliminary hyperlink that redirected 4 occasions ultimately touchdown on an attacker-controlled docusigning[.]kirklandellis[.]internet web site.
“The included HTML file within the assault sends the consumer to a WordPress occasion that has recursive redirection functionality. As of this writing, we’re not certain if this particular WordPress set up has been compromised or a plugin was put in to open this redirect location,” said Cloudflare.
Among the many firm’s suggestions is a suggestion to encourage finish consumer vigilance on ACH (Automated Clearing Home) or SWIFT (Society for Worldwide Interbank Monetary Telecommunication) associated messages.
“Given its massive scale prevalence, ACH & SWIFT phish are frequent ways leveraged by risk actors to redirect funds to themselves,” mentioned Cloudflare. The corporate mentioned it hadn’t but seen any massive scale ACH campaigns using the SVB model, however that doesn’t imply such schemes aren’t imminent.
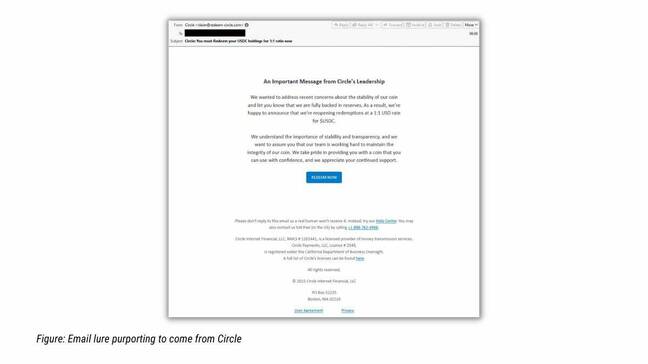
American cybersecurity agency Proofpoint said on Tuesday it’s researchers had tracked “a marketing campaign leveraging lures associated to USD Coin (USDC), a digital stablecoin tied to USD that was impacted by the SVB collapse.”
Malicious SendGrid accounts despatched messages impersonating cryptocurrency manufacturers and requested victims to say their crypto by URLs that had been redirected.
“Clicking the button would attempt to open a DeFi URL, so the sufferer would wish to have a DeFi handler put in, corresponding to MetaMask pockets. The sufferer would then be lured to put in a Sensible Contract that might switch the contents of the sufferer’s pockets to the attacker,” mentioned Proofpoint.
In accordance with the agency, As soon as Circle, the corporate which points USD Coin (USDC), introduced it had money reserves in SVB, the risk actor began spoofing the fintech firm with a lure promising 1:1 USDC to USD redemption.
“Proofpoint recommends that anybody concerned in dealing with monetary data or transactions train further warning and diligence as messages might emanate from fraudsters,” tweeted the corporate. ®