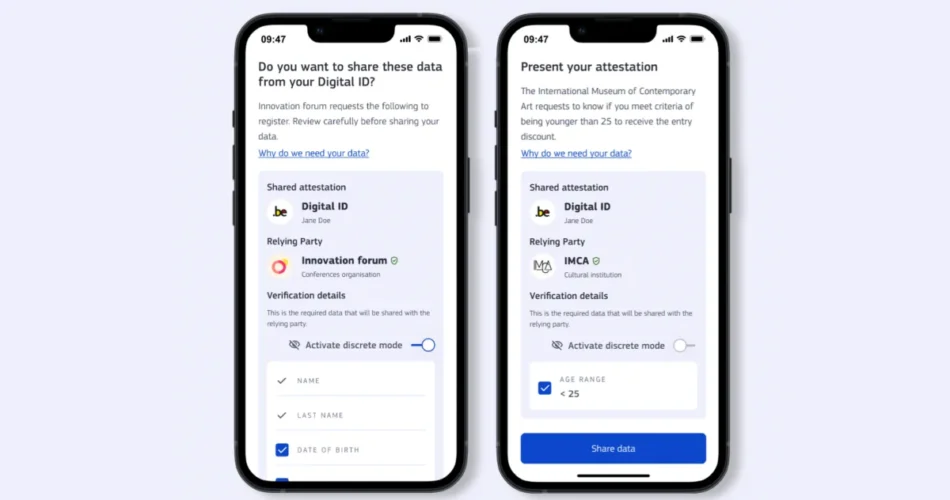
The European Fee unveiled detailed technical specs on July 14, 2025, for an EU-wide age verification system that can require digital identification credentials to entry web sites containing grownup content material. The announcement comes simply weeks earlier than the UK’s On-line Security Act triggered a 1,400% surge in VPN signups, in accordance with Proton VPN knowledge reported on July 25, 2025.
The timing demonstrates how swiftly regulatory frameworks are increasing throughout Europe. Following the UK’s implementation of necessary age verification for grownup content material platforms on January 17, 2025, the European Union has accelerated its personal digital identification necessities by the Digital Companies Act (DSA) framework, with full implementation scheduled for completion by the tip of 2026.
Subscribe the PPC Land e-newsletter ✉️ for comparable tales like this one. Obtain the information on daily basis in your inbox. Freed from advertisements. 10 USD per 12 months.
In keeping with the European Commission’s technical documentation, the brand new system will function as a “white-label answer” developed by the T-Scy consortium, composed of Swedish software program agency Scytales AB and German firm T-Systems International GmbH, a subsidiary of Deutsche Telekom. Denmark, France, Greece, Italy and Spain will pilot the expertise first, with broader implementation scheduled throughout all 27 EU member states by the tip of 2026.
The Deutsche Telekom connection extends past technical infrastructure growth into broader digital identification initiatives. T-Methods’ mother or father firm operates UTIQ, a telecommunications-based identification verification system that has already established partnerships with main European carriers together with Orange, Telefónica, and Vodafone. UTIQ’s current network-level authentication capabilities place Deutsche Telekom’s subsidiary to combine age verification performance with established telecommunications infrastructure, probably enabling seamless credential verification throughout cell and broadband networks all through Europe.
The technical structure represents a big departure from conventional age verification strategies. In keeping with the fee’s framework, the system will operate as a precursor to the EU Digital Identification Pockets, requiring customers to show they’re over 18 with out revealing further private info to service suppliers.
Privateness issues drive technical innovation
The system addresses rising privateness issues that emerged in the course of the UK’s implementation. Privacy-conscious consumers increasingly opt for VPN services quite than submitting authorities identification paperwork to confirm their age for accessing grownup content material.
Nonetheless, the involvement of Deutsche Telekom by T-Methods raises questions on telecommunications corporations’ entry to identification verification knowledge. Whereas the EU’s technical specs emphasize privacy-preserving design, T-Methods’ position in growing the verification infrastructure may probably present Deutsche Telekom with insights into person verification patterns, even when particular person identities stay protected by cryptographic protocols. The corporate’s current UTIQ network-level authentication system already processes subscriber identification knowledge throughout a number of European carriers, creating potential knowledge correlation alternatives regardless of technical privateness safeguards.
UTIQ’s technical structure demonstrates how telecommunications corporations can entry network-level indicators that correlate with person identities. In keeping with UTIQ’s documentation, the system generates a “Community Sign” from customers’ telecom connections, which then creates a “consentpass” that permits cross-device monitoring by “martechpass” and “adtechpass” identifiers. Whereas UTIQ claims it “has no means to entry or determine the person” from the Community Sign, the telecommunications operators offering these indicators inherently possess the connection knowledge that hyperlinks community exercise to particular person subscribers. This current functionality may prolong to age verification methods, the place T-Methods may correlate verification requests with subscriber identities even inside privacy-preserving frameworks.
In keeping with the European Knowledge Safety Board’s Assertion 1/2025, adopted on February 11, 2025, organizations should implement strict knowledge safety ideas when deploying age verification methods. The assertion establishes complete pointers for safeguarding private knowledge whereas figuring out customers’ ages on-line.
Jason Nurse, a cyber professional on the College of Kent, expressed issues about knowledge safety implications in the course of the UK implementation: “These websites shall be entrusted with storing massive quantities of personally identifiable info from probably huge segments of the inhabitants. How can we be assured this knowledge will not be misused? Such centralised databases create engaging targets for attackers looking for info for blackmail, extortion or different malicious functions.”
The EU’s method makes an attempt to handle these issues by technical design. In keeping with the fee’s documentation, when customers activate the app, their age shall be verified by the issuer utilizing detailed private knowledge, just like the date of delivery. Nonetheless, on-line providers will solely obtain a proof that the person is over 18, with out every other private particulars.
Technical implementation creates enforcement challenges
The EU system builds upon the Digital Services Act, which turned totally operational for all platforms on February 17, 2024. Article 28(1) requires on-line platforms accessible to minors to make sure “a excessive stage of privateness, security and safety” for underage customers.
Not like the UK’s fast enforcement method, the EU has structured implementation by a phased pilot program. Consumer testing started in late June 2025 with assist from EU Safer Web Centres, in accordance with fee statements. The pilot part permits for technical refinement earlier than necessary compliance necessities take impact.
The fee’s pointers specify that “strategies that depend on verified and trusted government-issued IDs might represent an efficient age verification technique, such because the EU Digital Identity Wallet.” This represents a extra centralized method in comparison with the UK’s reliance on particular person platform verification methods.
Platform responses reveal various compliance methods. Bluesky announced on July 10, 2025, that it will implement Epic Video games’ Youngsters Net Companies for UK customers, requiring bank card verification and face scans. Reddit deployed comparable measures by Persona, a third-party verification specialist, providing both selfie uploads with biometric age estimation or authorities ID verification.
Subscribe the PPC Land e-newsletter ✉️ for comparable tales like this one. Obtain the information on daily basis in your inbox. Freed from advertisements. 10 USD per 12 months.
Enforcement mechanisms mirror UK penalties
The EU framework contains substantial monetary penalties just like these carried out within the UK. In keeping with Digital Companies Act provisions, corporations can face fines as much as €18 million or 10 p.c of their qualifying worldwide income, whichever is larger. Platform operators additionally face potential prison legal responsibility for senior managers who fail to adjust to info requests.
Popular dating app exposes 72,000 identity documents in security breach
Verification system stored users’ selfies and government IDs without proper security measures, highlighting privacy risks in mandatory age checks.

The fee possesses further enforcement instruments together with enterprise disruption measures. In excessive instances, regulators can require “cost suppliers, advertisers and web service suppliers to cease working with a website, stopping it from producing cash or being accessed” from EU territories.
Visa and Mastercard become enforcement arms of UK online safety regulations
Financial networks now implementing government censorship policies across digital platforms, from Steam to adult content sites.

This enforcement framework extends past the UK’s method by incorporating cross-border coordination mechanisms. In keeping with the Digital Companies Act construction, nationwide regulators throughout all 27 member states should coordinate enforcement actions for platforms working throughout a number of jurisdictions.
Advertising business faces operational challenges
The implementation creates important implications for digital advertising and marketing operations throughout Europe. Age verification necessities introduce further friction in person onboarding processes that might have an effect on conversion charges and promoting effectiveness.
European websites achieve “North Korean consent rates” through payment barriers
Companies charge users to refuse tracking while generating only 0.82% revenue increase for news publishers.

Digital marketing professionals now navigate complicated compliance necessities as platforms implement various verification approaches. The requirement for strong verification methods alters person acquisition prices and viewers concentrating on capabilities for corporations working in regulated markets.
Compliance prices create explicit challenges for smaller platforms and non-profit organizations. Implementation bills related to age verification methods set up potential boundaries to entry for rising platforms, whereas established corporations can distribute compliance prices throughout bigger person bases.
The regulatory framework impacts promoting expertise suppliers as effectively. Corporations should adapt monitoring mechanisms to accommodate customers who entry platforms by VPN providers or different verification strategies, probably impacting knowledge high quality and attribution accuracy.
Technical structure requires infrastructure overhaul
The EU’s technical specs element a modular framework designed for integration throughout a number of service sorts. In keeping with fee documentation, the system helps “safe integration into numerous providers, together with cell apps, web sites, and telco platforms.”
The structure depends on cryptographic verification protocols and zero-knowledge proofs to forestall cross-service monitoring. Every verification proof features solely as soon as, stopping platforms from constructing complete person profiles throughout completely different providers.
T-Methods and Scytales have revealed technical documentation to information potential adopters in the course of the beta testing part. The system operates below the EUPL-1.2 license, making the supply code freely accessible for modification and integration by market contributors.
Member states preserve flexibility in customizing the answer for nationwide contexts. In keeping with fee pointers, nations can prolong age verification past the baseline 18-year threshold or incorporate further use instances comparable to alcohol purchases or playing entry.
Worldwide regulatory coordination accelerates
The EU’s method displays broader worldwide coordination on digital security rules. The timing follows intensive session between European authorities and UK regulators in the course of the On-line Security Act’s growth part.
In keeping with the European Knowledge Safety Board, the framework incorporates classes realized from France’s earlier restrictions on grownup content material entry and the UK’s preliminary implementation challenges. French privateness authorities beforehand declared enhanced surveillance methods neither essential nor proportionate for age verification, citing GDPR violations and surveillance issues.
The fee’s framework makes an attempt to steadiness these competing necessities by technical design quite than regulatory exemptions. Privateness-preserving applied sciences allow age verification whereas sustaining knowledge safety requirements throughout completely different nationwide jurisdictions.
The method contrasts with different worldwide frameworks. United States lawmakers have launched a number of baby security payments with out establishing unified technical requirements, whereas a number of Asian nations develop separate digital identification and baby safety methods.
Implementation timeline creates compliance stress
The fee’s timeline offers restricted preparation durations for affected platforms. With pilot testing concluding by the tip of 2025 and necessary implementation scheduled for 2026, corporations face compressed growth schedules for compliance methods.
In keeping with technical documentation, platforms should combine verification protocols that assist a number of authentication strategies whereas sustaining person expertise requirements. The requirement for seamless integration throughout desktop and cell platforms provides complexity to implementation necessities.
Smaller platforms face explicit challenges assembly the timeline necessities. Not like main social media corporations with intensive engineering sources, smaller providers should steadiness compliance investments in opposition to operational sustainability in the course of the transition interval.
The regulatory timeline coincides with broader Digital Companies Act obligations. Corporations should concurrently implement content material moderation necessities, transparency reporting mechanisms, and danger evaluation procedures alongside age verification methods.
Privateness advocates specific implementation issues
Regardless of privacy-preserving design ideas, digital rights organizations preserve skepticism concerning the broader implications of necessary age verification. The requirement for government-issued identification paperwork to entry authorized grownup content material represents a big departure from nameless web entry ideas.
The correlation between VPN utilization spikes and age verification implementation demonstrates person resistance to identification disclosure necessities. Proton VPN reported sustained elevated signup charges quite than non permanent will increase, suggesting everlasting behavioral adjustments amongst UK customers.
Technical circumvention strategies proceed evolving as customers adapt to regulatory restrictions. VPN providers, different consumer purposes, and browser modifications present workarounds that probably undermine the effectiveness of age verification necessities.
The EU’s technical method makes an attempt to handle privateness issues by architectural design quite than regulatory exemptions. Whether or not this steadiness proves ample for person acceptance stays unsure as implementation proceeds throughout member states.
EU Digital Identification Pockets emerges as cornerstone expertise
The age verification system represents the primary sensible implementation of the European Digital Identification Pockets framework, scheduled for necessary deployment throughout all member states by December 2026. In keeping with the European Fee’s roadmap, the EUDIW will essentially remodel how residents work together with digital providers all through the continent.
The pockets features as a complete digital identification answer enabling residents to retailer and current verified credentials with out counting on personal sector platforms. In keeping with fee documentation, “The European Digital Identification shall be accessible to EU residents, residents, and companies who wish to determine themselves or present affirmation of sure private info.”
Member states face strict implementation deadlines below the revised eIDAS regulation. The framework requires nationwide governments to supply digital identification options to at the very least 80% of residents by 2030, creating unprecedented coordination challenges throughout numerous technical infrastructures.
The technical structure builds upon current nationwide identification methods whereas establishing interoperability requirements. In keeping with the fee’s specs, the pockets will assist numerous credential sorts together with driving licenses, academic certificates, skilled {qualifications}, and well being information alongside age verification capabilities.
EUDIW roadmap accelerates amid regulatory stress
Implementation timelines have compressed considerably because the authentic 2021 proposal. The fee initially projected gradual rollout by 2027, however regulatory necessities from the Digital Companies Act and On-line Security coordination have accelerated deployment schedules.
Pilot packages throughout a number of member states started testing core performance in the course of the first quarter of 2025. In keeping with technical documentation, these trials give attention to cross-border interoperability and integration with current nationwide identification infrastructure.
The massive-scale pilot part includes over 250 personal and public organizations throughout completely different sectors. Collaborating entities embody banks, telecommunications corporations, academic establishments, and authorities businesses testing numerous use instances for digital credential presentation.
Technical specs launched in early 2025 element necessities for pockets suppliers, credential issuers, and relying events. The framework mandates compliance with worldwide requirements together with W3C Verifiable Credentials and decentralized identifier protocols.
Infrastructure transformation reshapes internet structure
The EUDIW implementation will essentially alter how web sites and purposes deal with person authentication and knowledge assortment. Conventional username-password methods face displacement by cryptographic credential presentation protocols.
In keeping with the fee’s technical framework, web sites will combine with standardized APIs for requesting particular person attributes with out accessing underlying private knowledge. This architectural shift strikes verification features from platform-specific implementations to standardized governmental infrastructure.
The transformation impacts basic internet applied sciences. Present cookie-based monitoring mechanisms turn into out of date when customers current verified credentials by standardized protocols. Promoting expertise suppliers should adapt attribution methods to accommodate nameless credential presentation quite than persistent person identifiers.
Platform operators will lose direct entry to person verification knowledge at present collected throughout account creation processes. In keeping with the EUDIW specs, service suppliers obtain solely particular attribute confirmations quite than complete private info databases.
Technical implementation creates systemic dependencies
The pockets system introduces single factors of failure throughout European digital infrastructure. When nationwide identification methods expertise outages, residents lose entry to all providers requiring credential presentation, from banking purposes to social media platforms.
Cross-border interoperability necessities create complicated technical dependencies between member state methods. In keeping with the eIDAS framework, a credential issued in France should operate seamlessly for providers hosted in Germany, requiring fixed synchronization between nationwide infrastructures.
The technical structure depends on cryptographic key administration throughout hundreds of thousands of particular person wallets. In keeping with safety specs, customers who lose entry to their cryptographic keys face prolonged restoration processes involving a number of governmental authorities.
Backend infrastructure necessities scale dramatically as adoption will increase. The fee estimates that peak utilization durations may generate a whole bunch of hundreds of thousands of simultaneous credential displays, requiring huge server capability throughout all member states.
Privateness implications problem conventional internet assumptions
The EUDIW framework essentially alters privateness assumptions underlying present internet structure. Customers acquire unprecedented management over private knowledge disclosure whereas governments receive complete visibility into citizen digital actions.
In keeping with privateness documentation, the pockets permits selective disclosure of particular attributes with out revealing further info. Residents can show their age for accessing grownup content material with out disclosing their precise birthdate, deal with, or different figuring out info to service suppliers.
Nonetheless, the centralized structure creates complete audit trails of citizen digital actions. In keeping with technical specs, pockets methods preserve logs of credential displays for safety and regulatory compliance functions.
The framework shifts privateness trade-offs from industrial knowledge assortment to governmental oversight. Whereas personal platforms lose entry to detailed person info, nationwide authorities acquire visibility into complete digital conduct patterns throughout their populations.
Business implications threaten current enterprise fashions
The EUDIW deployment challenges basic assumptions underlying digital promoting and person analytics. Platforms at present depend on persistent person identifiers for concentrating on and measurement, capabilities that turn into not possible below nameless credential presentation protocols.
In keeping with business evaluation, promoting expertise corporations face substantial income impacts as concentrating on precision decreases. The lack to construct complete person profiles throughout a number of providers reduces promoting effectiveness and pricing energy for digital platforms.
Knowledge brokerage industries face potential elimination because the EUDIW framework prevents assortment and aggregation of private info throughout completely different sources. Corporations specializing in client knowledge analytics should adapt enterprise fashions to function inside nameless credential methods.
Buyer relationship administration methods require basic redesign to accommodate nameless person interactions. Conventional advertising and marketing automation platforms can’t operate when customers current completely different nameless credentials for every interplay.
Safety structure introduces new assault vectors
The EUDIW system creates engaging targets for stylish risk actors looking for to compromise nationwide identification infrastructure. Profitable assaults in opposition to pockets methods may allow identification theft on unprecedented scales throughout total populations.
In keeping with safety assessments, the cryptographic protocols defending credential presentation turn into targets for nation-state adversaries looking for intelligence gathering capabilities. Compromised pockets methods may allow international governments to observe citizen actions throughout a number of nations.
The technical implementation introduces complexity that will increase vulnerability surfaces. In keeping with cybersecurity evaluation, the interplay between a number of cryptographic protocols, cross-border communication methods, and numerous nationwide infrastructures creates quite a few potential failure factors.
Phishing assaults will evolve to focus on pockets credential presentation quite than conventional password harvesting. Malicious actors can create fraudulent providers requesting pointless credential displays to construct complete sufferer profiles.
Interoperability challenges fragment implementation
Technical coordination throughout 27 completely different nationwide methods creates substantial implementation complexities. Every member state maintains distinct technical infrastructure, regulatory frameworks, and cultural approaches to digital identification administration.
In keeping with the fee’s coordination documentation, reaching seamless interoperability requires intensive standardization efforts throughout numerous governmental methods. Technical specs should accommodate various nationwide necessities whereas sustaining purposeful consistency.
Legacy system integration presents important challenges for member states with current digital identification infrastructure. International locations should adapt present methods to assist EUDIW protocols whereas sustaining backward compatibility with established governmental providers.
The framework requires coordination with third-country methods for worldwide commerce and journey purposes. Technical protocols should assist credential presentation to non-EU providers whereas sustaining safety and privateness requirements.
Financial transformation accelerates digital divide
The necessary nature of EUDIW implementation creates financial pressures for residents unable to adapt to digital-first governance. Aged populations and people with restricted technical literacy face potential exclusion from important providers.
In keeping with demographic evaluation, the requirement for smartphone-based credential presentation disadvantages populations missing entry to suitable units. Rural areas with restricted web connectivity face explicit challenges accessing wallet-dependent providers.
Small companies encounter substantial compliance prices adapting methods to assist EUDIW integration. In keeping with financial affect assessments, the technical necessities for credential verification create boundaries for enterprises missing devoted technical sources.
The implementation timeline coincides with broader digital transformation necessities throughout a number of regulatory frameworks. Corporations should concurrently adapt to EUDIW protocols, Digital Companies Act obligations, and numerous nationwide compliance necessities.
Advantages promise enhanced person management and safety
Regardless of implementation challenges, the EUDIW framework presents important benefits for citizen privateness and safety in comparison with present industrial knowledge assortment practices. Customers acquire unprecedented management over private info disclosure and may confirm their credentials with out counting on personal sector intermediaries.
The system eliminates password-related safety vulnerabilities that at present plague internet authentication. In keeping with safety evaluation, cryptographic credential presentation offers stronger authentication than conventional username-password combos whereas lowering phishing assault effectiveness.
Cross-border mobility improves considerably as residents can current verified credentials seamlessly throughout EU member states. The framework eliminates bureaucratic boundaries for accessing providers whereas touring or relocating inside European territories.
The structure reduces dependency on industrial platforms for identification verification. Residents now not have to create accounts with a number of personal corporations to entry important providers, lowering publicity to company knowledge breaches and privateness violations.
Regulatory coordination establishes international precedent
The EU’s complete method to digital identification establishes a regulatory mannequin that different jurisdictions will doubtless undertake or adapt. The technical requirements and privateness frameworks developed for EUDIW may affect worldwide approaches to digital identification administration.
In keeping with coverage evaluation, the success or failure of EUDIW implementation will considerably affect international attitudes towards government-managed digital identification methods. Different democratic societies will consider European outcomes when growing their very own frameworks.
The system’s privacy-preserving structure presents an alternative choice to surveillance-oriented digital identification approaches carried out by authoritarian governments. The technical design ideas prioritize citizen privateness whereas enabling essential identification verification capabilities.
Worldwide coordination mechanisms inside the EUDIW framework may facilitate broader adoption of suitable methods. Technical interoperability requirements may allow credential presentation throughout completely different governmental digital identification methods globally.
Timeline
- October 26, 2023: UK On-line Security Act receives Royal Assent
- February 17, 2024: Digital Companies Act turns into totally operational for all EU platforms
- January 17, 2025: Age verification duties for UK Half 5 providers take impact
- February 11, 2025: European Data Protection Board releases comprehensive age verification guidance
- March 17, 2025: Ofcom features full enforcement powers for unlawful content material duties in UK
- July 10, 2025: Bluesky announces UK age verification implementation
- July 14, 2025: European Fee releases EU age verification blueprint
- July 25, 2025: Proton VPN studies 1,400% signup surge from UK customers
- Finish 2025: EU pilot testing part concludes throughout 5 member states
- Finish 2026: EU Digital Identification Pockets necessary implementation deadline
Key Phrases Defined
Age Verification
Age verification represents the technical and procedural mechanisms that on-line platforms should implement to forestall minors from accessing grownup content material. Below each the UK’s On-line Security Act and the EU’s Digital Companies Act, these methods should meet strong requirements outlined by regulatory authorities, requiring platforms to confirm customers’ ages by dependable strategies earlier than granting entry to restricted materials. The expertise encompasses numerous approaches together with authorities ID verification, biometric age estimation, bank card checks, and rising cryptographic proof methods that allow age affirmation with out revealing particular private particulars.
Digital Companies Act (DSA)
The Digital Companies Act constitutes the European Union’s complete legislative framework for regulating on-line platforms and digital providers throughout all 27 member states. Enacted in 2022 and turning into totally operational in February 2024, the DSA establishes necessary obligations for platforms to guard customers from dangerous content material, implement clear content material moderation practices, and guarantee particular protections for minors. Article 28 particularly requires platforms accessible to kids to take care of excessive ranges of privateness, security, and safety, creating the authorized basis for necessary age verification necessities all through Europe.
EU Digital Identification Pockets (EUDIW)
The EU Digital Identification Pockets represents a government-issued digital credential system that can allow residents to retailer and current verified identification attributes with out counting on personal sector platforms. Scheduled for necessary implementation throughout all member states by December 2026, the pockets will assist numerous credential sorts together with age verification, academic certificates, skilled {qualifications}, and well being information. The system operates by cryptographic protocols that allow selective disclosure of particular attributes whereas sustaining person privateness and stopping cross-service monitoring.
European Fee
The European Fee features as the chief department of the European Union, liable for proposing laws and overseeing implementation of digital coverage throughout member states. Within the context of age verification and digital identification, the Fee coordinates technical requirements, develops implementation pointers, and manages cross-border interoperability necessities. The Fee’s position contains establishing the technical specs for age verification methods, coordinating with nationwide regulators, and guaranteeing constant software of digital rights protections all through European territories.
On-line Security Act
The UK’s On-line Security Act 2023 represents complete web regulation laws that requires platforms with UK connections to implement security methods for safeguarding customers, particularly kids, from on-line harms. The Act creates legally binding obligations for social media corporations, search providers, and grownup content material platforms, with enforcement powers together with substantial monetary penalties and potential prison legal responsibility for executives. The laws’s implementation on January 17, 2025, triggered important person conduct adjustments together with huge VPN adoption as residents sought to avoid age verification necessities.
Privateness
Privateness issues in digital age verification embody the gathering, storage, and potential misuse of delicate private info required for identification affirmation. Conventional verification strategies require customers to submit authorities identification paperwork, creating complete databases of private info that turn into engaging targets for cybercriminals and lift surveillance issues. The EU’s method makes an attempt to handle these points by privacy-preserving applied sciences that allow age affirmation with out revealing pointless private particulars, although centralized governmental oversight introduces completely different privateness trade-offs.
Technical Implementation
Technical implementation refers back to the complicated technological infrastructure required to deploy age verification and digital identification methods throughout numerous platforms and nationwide boundaries. This encompasses cryptographic protocols, API requirements, cross-border interoperability mechanisms, and integration with current governmental identification methods. The technical structure should steadiness safety necessities, person expertise issues, privateness protections, and scalability calls for whereas accommodating various nationwide technical infrastructures and regulatory frameworks throughout completely different jurisdictions.
Compliance
Compliance represents the necessary adherence to regulatory necessities governing digital platforms’ operations, content material moderation practices, and person safety measures. Below each UK and EU frameworks, platforms face substantial monetary penalties, potential prison legal responsibility for executives, and attainable enterprise disruption measures for failing to fulfill age verification and security obligations. Compliance prices create explicit challenges for smaller platforms and non-profit organizations that should steadiness regulatory investments in opposition to operational sustainability whereas adapting to compressed implementation timelines.
VPN Companies
VPN (Digital Personal Community) providers allow customers to masks their geographic location and encrypt web site visitors, successfully circumventing location-based content material restrictions and age verification necessities. The 1,400% surge in UK VPN signups following On-line Security Act implementation demonstrates person resistance to necessary identification disclosure for accessing authorized grownup content material. VPN adoption represents a big problem to the effectiveness of geographical content material restrictions, as customers can seem to browse from nations with completely different regulatory frameworks.
Enforcement
Enforcement encompasses the regulatory powers and mechanisms accessible to authorities for guaranteeing platform compliance with age verification and digital security necessities. Each UK and EU frameworks present substantial penalties together with fines as much as €18 million or 10% of worldwide income, prison prosecution of executives, and enterprise disruption measures requiring cost suppliers and web service suppliers to stop working with non-compliant platforms. Enforcement coordination throughout a number of jurisdictions creates complicated authorized frameworks for platforms working internationally whereas guaranteeing constant software of protecting measures for minors.
Subscribe the PPC Land e-newsletter ✉️ for comparable tales like this one. Obtain the information on daily basis in your inbox. Freed from advertisements. 10 USD per 12 months.
Abstract
Who: The European Fee, by the Digital Companies Act framework, concentrating on on-line platforms accessible to minors throughout all 27 EU member states. Technical growth dealt with by T-Scy consortium comprising Scytales AB (Sweden) and T-Methods Worldwide GmbH (Germany).
What: Implementation of necessary age verification necessities utilizing a standardized digital identification system for accessing grownup content material on-line. The system features as a “white-label answer” requiring customers to show they’re over 18 with out revealing further private info to service suppliers.
When: Technical specs launched July 14, 2025, with pilot testing throughout Denmark, France, Greece, Italy and Spain all through 2025. Full implementation necessary throughout all EU member states by the tip of 2026, coinciding with EU Digital Identification Pockets deployment.
The place: All 27 European Union member states, affecting each home and worldwide platforms serving EU customers. Preliminary pilot deployment in 5 nations earlier than continent-wide growth.
Why: Regulatory response to guard minors from accessing grownup content material on-line whereas addressing privateness issues that emerged in the course of the UK’s On-line Security Act implementation. The framework makes an attempt to steadiness baby safety aims with knowledge safety necessities by privacy-preserving technical structure.
Source link