New EDPB steerage outlines technical necessities for pseudonymisation in information processing whereas offering real-world examples.
The European Knowledge Safety Board (EDPB) published its Tips 01/2025 on pseudonymisation on January 16, 2025, marking the primary complete steerage on this information safety measure because the implementation of GDPR. The rules present detailed technical specs for organizations processing private information throughout the European Financial Space.
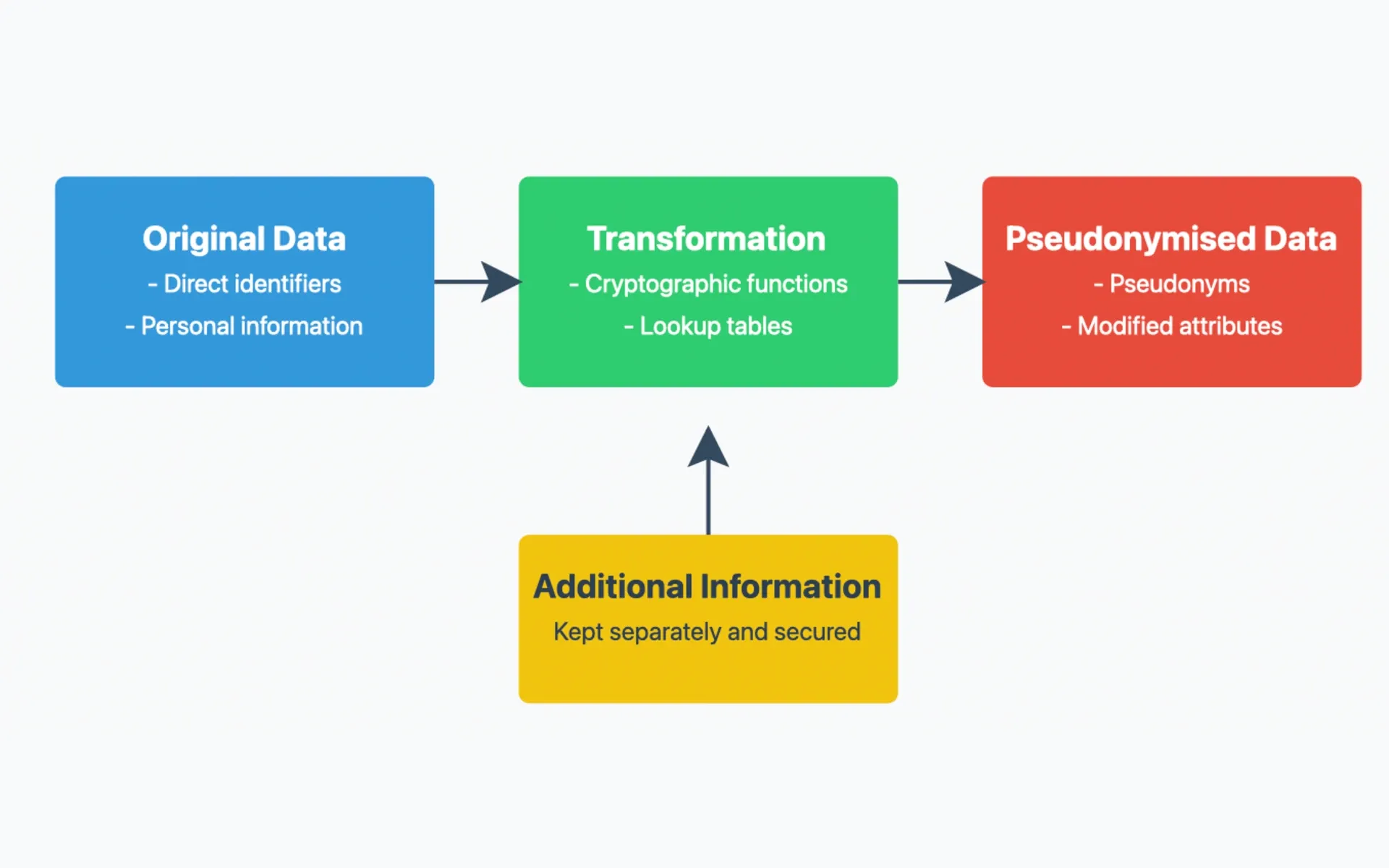
Based on the EDPB doc, pseudonymisation represents a big safeguard that controllers can implement to fulfill varied information safety obligations. The steerage defines pseudonymisation because the processing of non-public information in a fashion stopping attribution to particular people with out further info saved individually underneath strict technical controls.
The newly launched tips set up that pseudonymised information stays private information underneath GDPR Article 4(5), even when the extra info enabling re-identification is held by totally different entities. This interpretation carries substantial implications for cross-border information transfers and inner information processing workflows.
The EDPB steerage introduces the idea of a “pseudonymisation area” – the managed atmosphere the place organizations should stop information attribution to particular people. This area encompasses the technical techniques, organizational processes, and personnel concerned in information processing actions.
For cryptographic implementations, the rules specify that controllers should make use of both cryptographic one-way features like Message Authentication Codes (MACs) or encryption algorithms with enough entropy of their secret parameters. The EDPB notes that lookup tables signify an alternate strategy, although they require safe storage of probably massive units of non-public information.
The doc outlines three main mechanisms for pseudonymisation: particular person pseudonyms sustaining constant identifiers throughout all processing, relationship pseudonyms various by context, and transaction pseudonyms altering with every interplay. Every mechanism serves totally different threat mitigation functions whereas enabling particular varieties of information evaluation.
The rules set up strict necessities for the safety of “pseudonymisation secrets and techniques” – the cryptographic keys or lookup tables enabling re-identification. Organizations should implement technical and organizational measures guaranteeing these secrets and techniques stay inaccessible to unauthorized events throughout the pseudonymisation area.
For cross-border transfers, the EDPB mandates that pseudonymisation can function a supplementary measure solely when the info importer neither possesses nor can acquire the extra info wanted for re-identification. The steerage particularly addresses situations involving information transfers to international locations missing sufficient information safety requirements.
Relating to information topic rights, the rules make clear that people preserve their GDPR entry and portability rights for pseudonymised information except the controller demonstrates an incapability to determine the info topic underneath Article 11. Controllers should facilitate these rights whereas sustaining the safety of the pseudonymisation system.
The doc offers ten detailed implementation examples, starting from inner evaluation situations to cross-border switch instances. These examples illustrate sensible functions of pseudonymisation in healthcare, employment, and industrial contexts.
Organizations have till February 28, 2025, to submit suggestions on the rules by way of the EDPB’s public session course of. The ultimate model will set up binding interpretations for information safety authorities throughout the European Financial Space.
The EDPB emphasizes that pseudonymisation alone doesn’t guarantee GDPR compliance, however fairly serves as one part of a complete information safety technique. Controllers should consider the effectiveness of their pseudonymisation measures towards particular processing contexts and dangers.
Trade consultants observe the rules’ sensible significance. Based on Phil Lee, Managing Director at Digiphile, the steerage presents complicated technical necessities that will problem organizations implementing pseudonymisation in industrial environments.
The publication arrives amid rising regulatory scrutiny of worldwide information flows and rising emphasis on technical information safety measures. Organizations processing private information throughout the EEA should now consider their pseudonymisation practices towards these detailed necessities.
Source link




