The USA Authorities Nationwide Vulnerability Database (NVD) revealed an advisory a couple of vulnerability found within the WP Statistics WordPress plugin that impacts as much as 600,000 lively installations.
The vulnerability was assigned a medium risk degree rating of 6.5 out of a scale of 1 to 10, with degree 10 representing probably the most extreme vulnerability degree.
WP Statistics Cross-Web site Request Forgery (CSRF)
The WP Statistics plugin was discovered to include a Cross-Web site Request Forgery vulnerability that might permit an attacker to compromise a web site by activating or deactivating plugins.
A Cross-Web site Request Forgery is an assault that requires a registered web site person (comparable to an administrator) to carry out an motion like a clicking a hyperlink, which then permits an attacker to benefit from a safety hole.
The safety hole on this occasion is a “lacking or incorrect nonce validation.”
A WordPress nonce is a safety token that’s supplied to a registered person that enables that person to securely carry out actions that solely a registered person can do.
The WordPress developer pages explains the nonce with the instance of an administrator deleting a submit.
WordPress would possibly generate a URL like this when an administrator degree person deletes a submit.
Under is hypothetical instance of a URL generated when deleting a submit with an ID variety of 123:
http://instance.com/wp-admin/submit.php?submit=123&motion=trash
A registered WordPress web site admin would decide up a nonce and the URL, within the instance, could seem like this:
http://instance.com/wp-admin/submit.php?submit=123&motion=trash&_wpnonce=b192fc4204
That final half, &_wpnonce=b192fc4204, is the nonce.
So, what’s occurring is that the nonce is both lacking or not correctly validated inside the WP Statistics plugin and that creates a safety hole for a malicious hacker to use.
The Nationwide Vulnerability Database (NVD) explains it like this:
“The WP Statistics plugin for WordPress is susceptible to Cross-Web site Request Forgery in variations as much as, and together with, 13.1.1. This is because of lacking or incorrect nonce validation on the view() perform.
This makes it potential for unauthenticated attackers to activate and deactivate arbitrary plugins, through a solid request granted they will trick a web site administrator into performing an motion comparable to clicking on a hyperlink.”
CSRF Vulnerability Patch
WP Statistics plugin vulnerability impacts model as much as an together with 13.1.1. Nevertheless there have been quite a few safety fixes added since then, together with in model 13.2.11, plus further fixes after that.
The present model of the plugin is 14.0.1. At the moment solely 29.3% of customers are utilizing the hottest model.
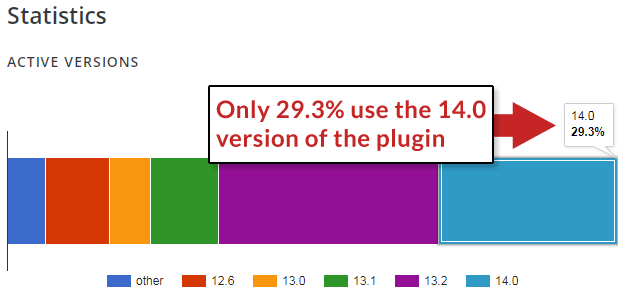
Customers of the outdated model of the plugin could need to contemplate updating to the newest model.
Learn the NVD safety advisory:
Featured picture by Shutterstock/Asier Romero
Source link


