Cybersecurity companies firm Group-IB Global Pvt. Ltd. has printed particulars on beforehand unreported phishing operations carried out by the nation-state cyber menace actor SideWinder between June and November 2021.
SideWinder, also called Rattlesnake, Hardcore Nationalist (HN2) and T-APT4, is a state-sponsored hacking group believed to be affiliated with the Indian authorities. The group has been concerned in numerous cyber espionage campaigns concentrating on a spread of industries, together with authorities companies, army organizations and vitality firms.
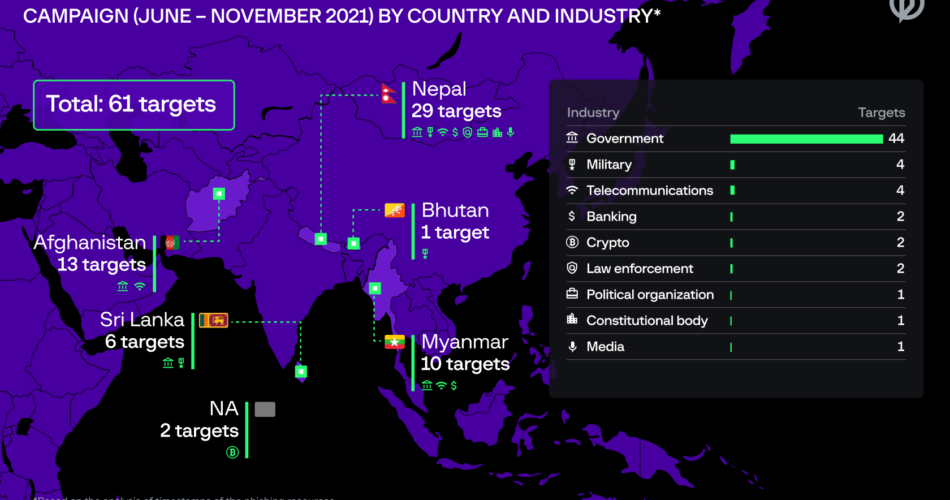
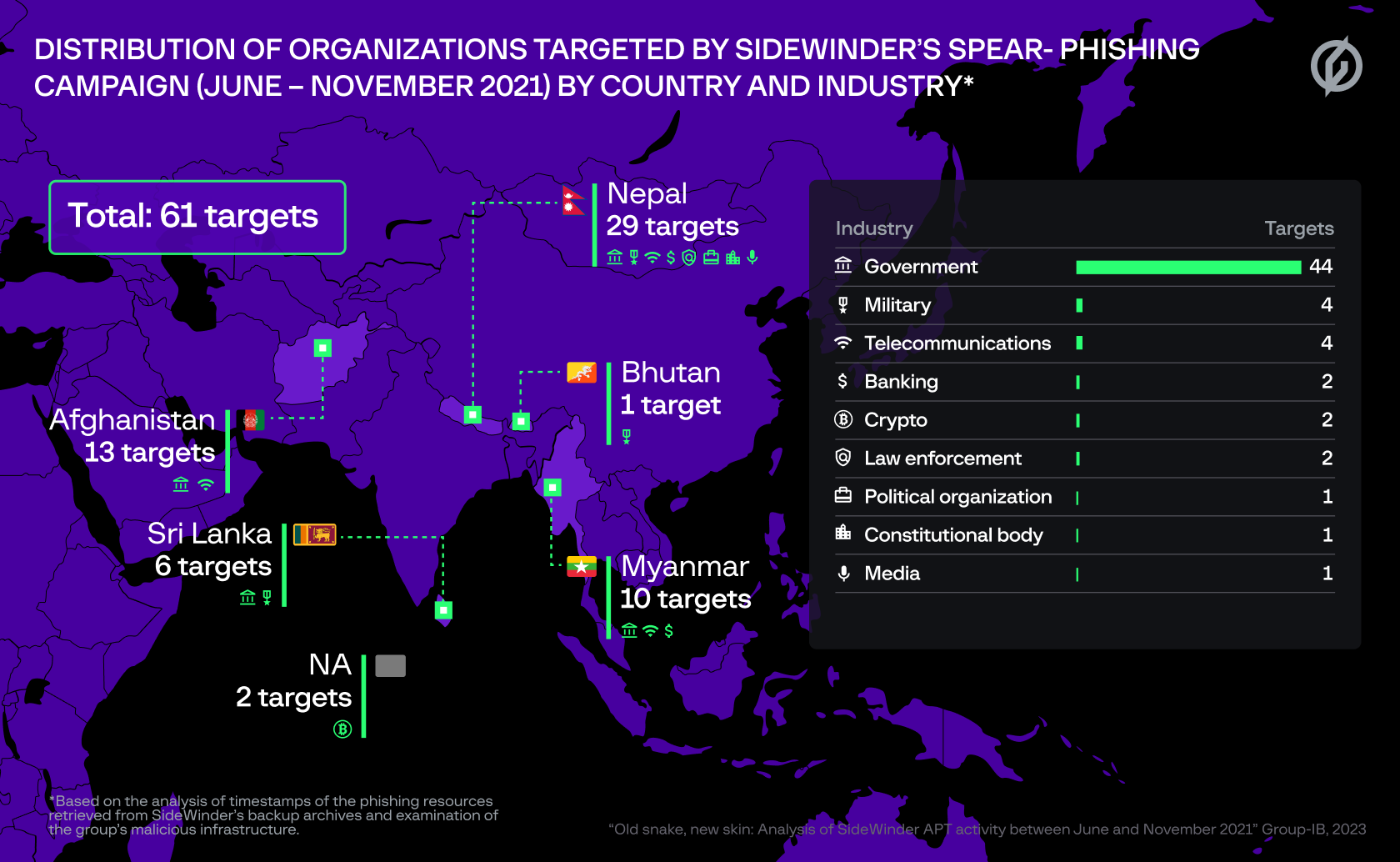
In response to Group-IB, the attackers tried to focus on 61 authorities, army, legislation enforcement and different organizations in Afghanistan, Bhutan, Myanmar, Nepal and Sri Lanka in 2021 (pictured). The marketing campaign concerned the hackers utilizing Telegram to obtain info from compromised networks.
Within the report “Outdated snake, new pores and skin: Evaluation of SideWinder APT exercise between June and November 2021,” Group-IB researchers confirmed hyperlinks between the SideWinder, Child Elephant, and Donot superior persistent menace teams and described the whole arsenal of the cyberespionage group, together with newly found instruments.
In June 2022, Group-IB found the group’s latest customized instrument, SideWinder.AntiBot.Script, which was utilized in beforehand documented phishing assaults towards Pakistani organizations. SideWinder is notable for its capacity to conduct a whole lot of espionage operations inside a brief interval.
Throughout proactive threat-hunting operations, the researchers found backup archives on infrastructure attributed to SideWinder. One of many 2021 archives contained a number of phishing initiatives designed to focus on authorities companies in Southeast Asia, amongst which have been pretend web sites imitating the Central Financial institution of Myanmar.
Based mostly on the date when the associated phishing pages have been edited, the Group-IB group was capable of reconstruct an approximate timeline of SideWinder’s phishing operations between June and November 2021. Because the phishing assets have been retrieved from a backup archive by the Group-IB group, there’s a risk that SideWinder’s assaults could have began earlier.
Additional evaluation allowed the Group-IB group to compile a listing of the group’s 61 potential targets, which embrace authorities, army, monetary, legislation enforcement, political, telecommunications and media organizations in Afghanistan, Bhutan, Myanmar, Nepal and Sri Lanka. It’s unknown whether or not any of those phishing campaigns have been profitable.
The researchers additionally found two phishing initiatives mimicking crypto firms. SideWinder’s rising curiosity in cryptocurrency could possibly be linked to the current makes an attempt to control the crypto market in India.
The complete report is primarily supposed for evaluation functions amongst cybersecurity consultants, however it supplies attention-grabbing perception into the nefarious cyber actions of the Indian authorities as effectively. Though a lot of the deal with hacking and cyber threats lands on international locations like Russia, China, North Korea and Iran, it’s useful to do not forget that all international locations — India and the U.S. included — sponsor these teams and hack different international locations.
Picture: Group-IB
Present your assist for our mission by becoming a member of our Dice Membership and Dice Occasion Neighborhood of consultants. Be a part of the group that features Amazon Net Companies and Amazon.com CEO Andy Jassy, Dell Applied sciences founder and CEO Michael Dell, Intel CEO Pat Gelsinger and lots of extra luminaries and consultants.
Source link