Confidential computing is a know-how that goals to boost information privateness and safety by offering encrypted computation on delicate information and isolating information from apps and different host sources in a fenced off enclave throughout processing. The idea of confidential computing is gaining recognition, particularly within the cloud computing house the place delicate information is commonly saved and processed.
Nonetheless, there are some who view confidential computing as an pointless know-how and a advertising ploy by cloud suppliers, geared toward calming prospects who’re cloud-phobic.
On this Breaking Evaluation, we revisit the notion of confidential computing and discover whether or not it’s simply advertising or a key a part of a trusted safety technique. To take action we’ll invite two Google LLC consultants to the present. However earlier than we get there, let’s summarize the general market local weather briefly with some Enterprise Know-how Analysis information.
Throughout the board, safety continues to be the No. 1 precedence
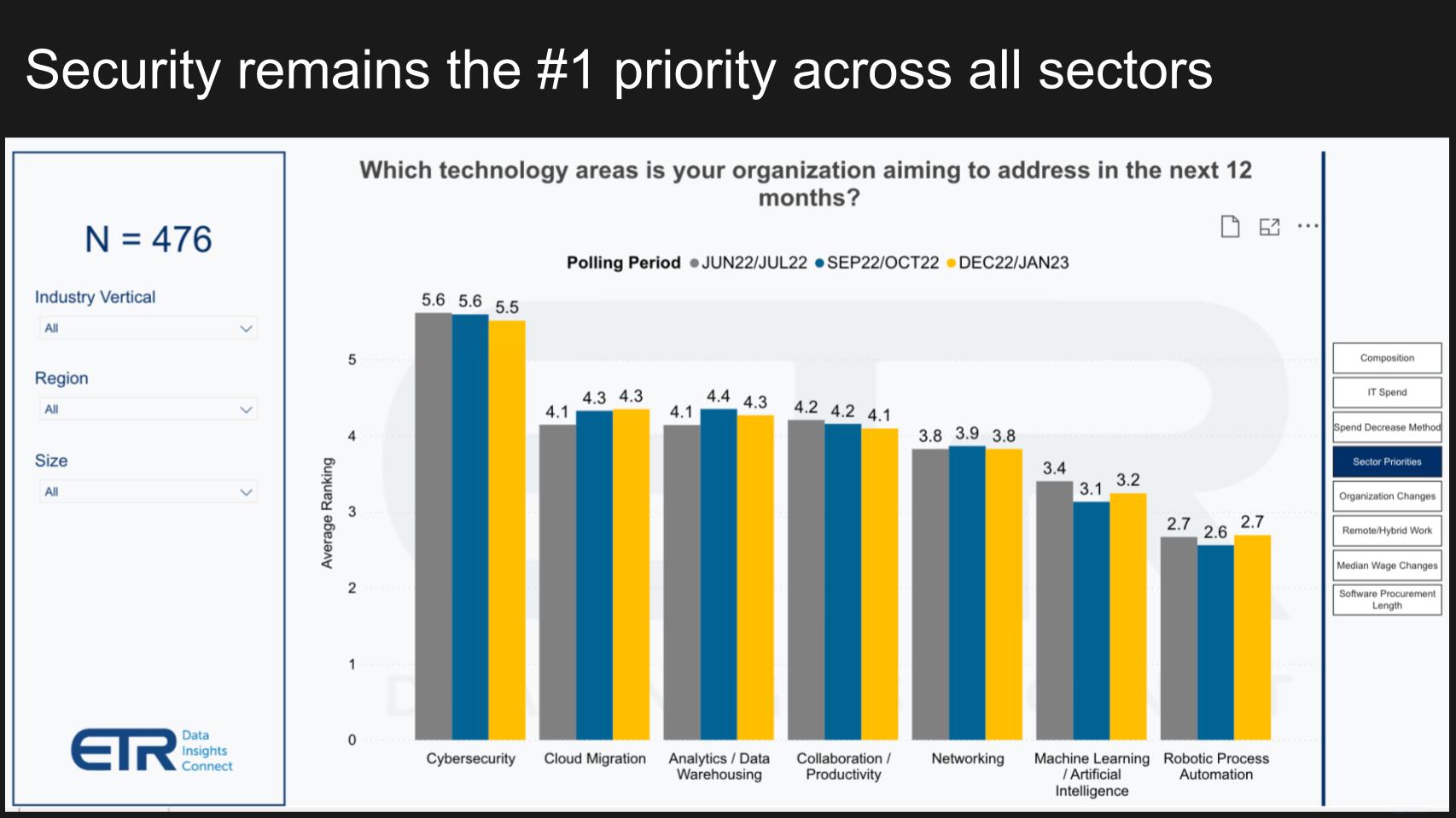
There’s not a ton within the ETR dataset on the subject of confidential computing. It’s a know-how that’s deeply embedded into silicon and computing architectures, so it’s not as seen to chief info officers and the data know-how choice makers in ETR’s quarterly surveys. However on the highest degree, safety stays the No. 1 precedence being addressed by organizations within the coming 12 months, as proven above.
That is just about throughout the board by trade, by area and by dimension of firm. The one slight deviation from the imply is in monetary companies. The second- and third-most-cited priorities, cloud migration and analytics, are noticeably nearer to cybersecurity than different sectors, seemingly as a result of monetary companies has at all times been hyper security-conscious. However safety continues to be a transparent No. 1 precedence in that sector.
Defending information in use: advertising hype or an actual want?
The thought behind confidential computing is to raised handle risk fashions for information in execution. Defending information at relaxation and information in transit have lengthy been a give attention to safety applied sciences, however extra just lately, silicon producers have launched architectures to separate information and functions from the host system. Arm Ltd., Intel Corp., Superior Micro Units Inc., Nvidia Corp. and different suppliers are all on board as are the massive cloud gamers and system producers resembling Dell Applied sciences Inc., IBM Corp. and Hewlett Packard Enterprise Co.
The argument towards confidential computing is that it narrowly focuses on reminiscence encryption and it doesn’t remedy the largest issues. A number of system photos, updates, totally different companies and the whole code circulation aren’t immediately addressed by reminiscence encryption. Slightly,11 to really assault these issues, many imagine that working methods should be reengineered with the attacker in thoughts. There are such a lot of variables and on the finish of the day, critics say the emphasis on confidential computing made by cloud suppliers is overstated and largely hype.
This tweet above from safety researcher @bsdaemon sums up the sentiment of many skeptics. He says:
Confidential computing is usually a advertising marketing campaign for reminiscence encryption. It’s not driving the trade in direction of the laborious, open issues… it’s promoting an phantasm.
Nonetheless, encrypting information in use and fencing off key parts of the system isn’t a foul factor… particularly if it comes with the package deal basically totally free.
The seller politics of confidential computing
There was an absence of standardization and interoperability between totally different confidential computing approaches and the Confidential Computing Consortium was established in 2019, ostensibly to speed up the market and affect requirements.
Notably, Amazon Internet Companies Inc. will not be a part of the consortium probably as a result of: 1) The politics of the consortium had been a conundrum for AWS as the bottom know-how outlined by the consortium is seen as limiting by AWS (our assertion, not AWS’); 2) Becoming a member of the consortium would validate a definition with which AWS isn’t aligned; and three) AWS might really feel it has a lead with its Annapurna acquisition and doesn’t need to validate its opponents.
Moreover, our analysis leads us to invest that AWS could also be working deep inside the U.S. authorities on a extra superior and complete definition of confidential computing that it probably intends to evolve as an official customary. It will be basic AWS to make a transfer like this as an aggressive and defensible technique round confidential computing that’s extremely differentiated from its competitors.
Google’s perspective on confidential computing
One of many premier members of the Confidential Computing Consortium is Google, together with many high-profile names, together with Arm, Intel, Meta Platforms Inc., Crimson Hat, Microsoft Corp. and others.
On this Breaking Evaluation, we’re happy to welcome two consultants on confidential computing from Google to unpack the subject: Nelly Porter, head of product for GCP Confidential Computing and Encryption, and Dr. Patricia Florissi, technical director within the Workplace of the CTO at Google Cloud.
What follows is a curated abstract of our dialog with the total video embedded beneath. After every query we embed a video clip of the solutions you possibly can look ahead to added context.
Q: Nelly after which Patricia, please describe your respective roles at Google Cloud.
Porter: I work on loads of attention-grabbing actions in Google with a give attention to safety and infrastructure safety. And we’re speaking about encryption and confidential computing is a crucial a part of the portfolio. As well as, I collaborate with Google colleagues and our prospects on safe software program provide chains. As a result of it is advisable belief your software program. Is it working safely in your confidential atmosphere? I work on having end-to-end confidence that your software program and your atmosphere are doing what you count on.
Florissi: I’m a technical director within the workplace of the CTO, OCTO for brief, in Google Cloud. And we’re a world group. We embody former CTOs like myself and senior technologists from giant companies, establishments and loads of profitable startups as nicely. And we have now two fundamental objectives. First, we work side-by-side with a few of our largest, most strategic prospects and we assist them remedy complicated engineering technical issues. And second, we focus with Google Cloud engineering and product administration on rising developments and applied sciences to information the trajectory of our enterprise. We’re a novel group as a result of we have now created this collaborative tradition with our prospects. And inside OCTO I spend loads of time collaborating with prospects and the trade at giant on applied sciences that may handle privateness, safety and sovereignty of information normally.
Watch and listen to Nelly and Patricia describe their respective roles in their own words.
Q: Nelly, what’s confidential computing from Google’s perspective – i.e. how do you outline it?
Porter: Confidential computing is without doubt one of the instruments in Google’s toolbox to assist prospects defend their information all through its total lifecycle. Confidential computing addresses the necessity to defend information and workloads. Not solely when it’s saved or in transit but additionally when it’s being processed and used within the cloud. With confidential computing, Google can present end-to-end safety of buyer information and workloads, guaranteeing the information stays safe whereas nonetheless with the ability to extract insights and course of it.
Watch Nelly Porter’s explanation of how Google defines confidential computing.
Q: Patricia, why do you assume this confidential computing is such an necessary know-how?
Florissi: Confidential computing is a crucial and transformative know-how as a result of it reduces the client’s risk boundaries and assault floor. It’s a pure development from encrypting information in transit and at relaxation, to now encrypting information whereas in use. Confidential computing permits organizations to collaborate with one another whereas retaining the confidentiality of the information, which is useful for all industries, not simply extremely regulated ones. For instance, in finance, bankers can collaborate to detect fraud whereas preserving the confidentiality and privateness of the information.
Q: Nelly, there’s a narrative on the market that claims confidential computing is a advertising ploy by cloud suppliers placating individuals with cloud phobia. Whilst you might strongly disagree, the argument is that confidential computing is simply reminiscence encryption and doesn’t handle many different issues. Additional, it’s overhyped by cloud suppliers. What would you say to this line of considering?
Not surprisingly, Porter strongly disagrees with the premise that confidential computing is simply advertising hype for reminiscence encryption. In line with Porter, the idea of confidential computing goes past simply the mechanism of defending buyer information. Confidential computing presents stronger safety for tenants in multitenant cloud environments by cryptographic isolation, which offers prospects with extra belief within the safety of their information. This cryptographic layer of isolation not solely protects prospects from different tenants within the atmosphere, but additionally from errors made by the software program supplier or potential zero-day assaults. By offering this layer of safety, confidential computing eliminates a few of the safety considerations that prospects might have when working their workloads in multitenant areas or collaborating with delicate information.
Q: Nelly, what’s architecturally totally different with confidential computing versus how working methods and digital machines have labored traditionally? Please clarify and we’ll put up this slide for context.
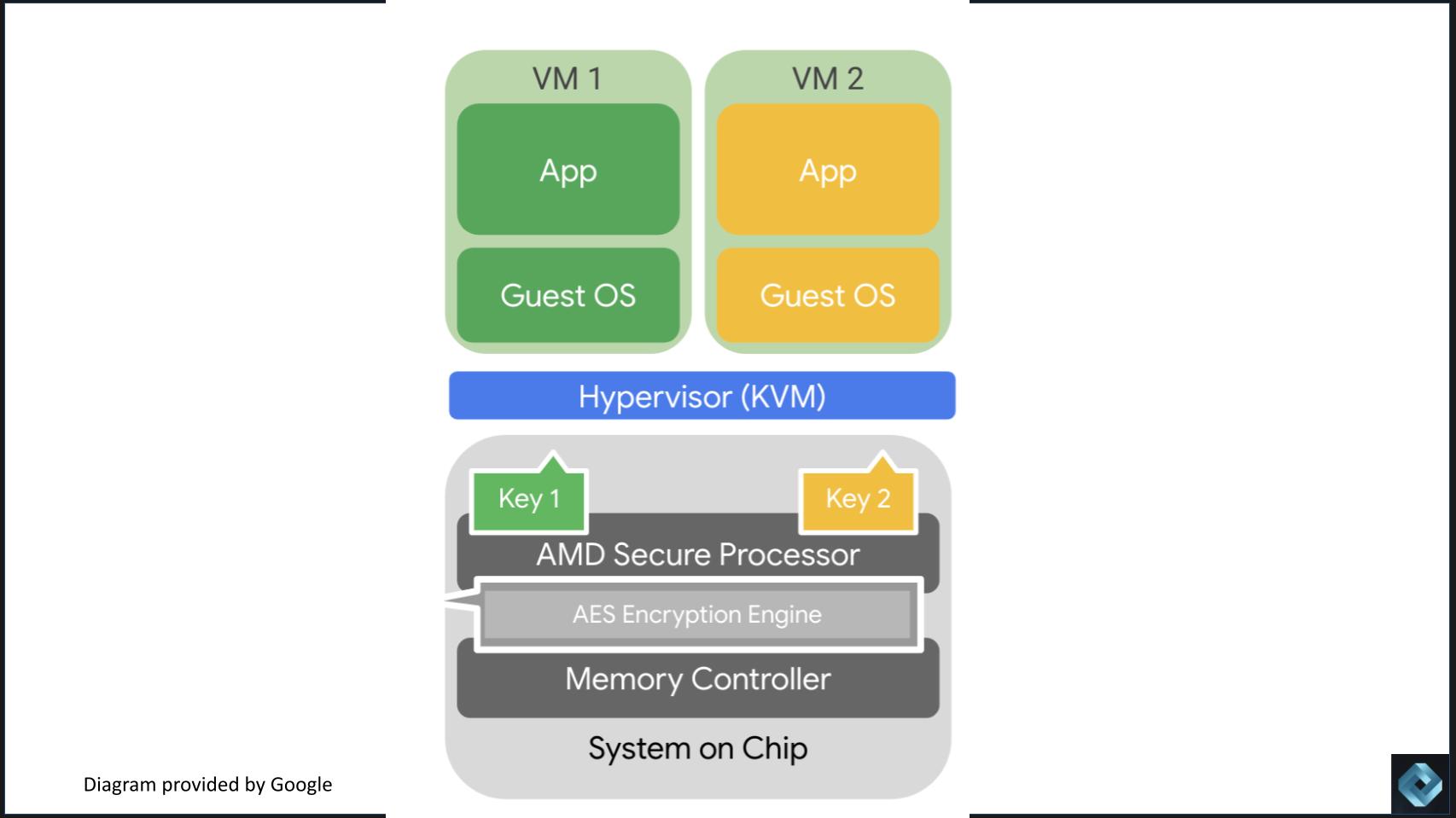
Porter: Google’s method to confidential computing is designed to protect three fundamental properties: 1) Clients don’t want to alter their code; 2) low latency; and three) scalability. To realize this, the whole system has to alter to supply the safety ensures of confidential computing. The next are the important thing architectural modifications in confidential computing:
- Root of belief: Making certain the integrity of the machine by the usage of ASICs that validate the configuration of the low-level system code and kernel. [Note: Porter mentioned Google’s Titan chip in this dialogue – watch the clip below for additional detail].
- Belief in silicon distributors: Validating the integrity of the firmware and software program of silicon distributors to make sure that the machine will not be modified or modified.
- Safe processor: Particular ASICs that generate a key for every VM, node or employee thread, which aren’t accessible to Google. The keys are random, ephemeral and saved in {hardware}.
- Encrypted reminiscence: The reminiscence is encrypted, however solely the safe processor has entry to the important thing, not Google. The info within the VM is in clear, however can’t be accessed exterior of the confidential field.
- Modified OS: The OS is modified to supply integrity and efficiency.
These modifications permit prospects to run their VMs with out altering their functions, with improbable efficiency and scalability, as they’d count on from a cloud supplier like Google.
Q: Patricia, what are the ensures that these hardware-based applied sciences present to cloud prospects?
Florissi: Google makes the next guarantees to its prospects with respect to confidential computing:
- Code and information confidentiality: Confidential computing ensures that the functions and information stay secret, with the reminiscence decrypting the information utilizing a key that’s ephemeral, per VM, and generated on demand.
- Code and information integrity: Confidential computing ensures that the appliance internals usually are not tampered with and that the workload processing the information preserves its integrity.
- Verifiable: Confidential computing offers attestation, which generates a log path that gives proof that the confidentiality and integrity of code and information had been preserved.
- Ceiling: Confidential computing ensures that the secrets and techniques have been preserved and never tampered with.
In line with Google, these ensures present prospects with the reassurance that their methods are shielded from unauthorized entry and that their information has not been corrupted or impacted by exterior actors.
Q: Nelly, how does Google make sure the compatibility of confidential computing with the present methods and functions?
Porter: To make sure compatibility with present functions with regards to confidential computing, Google has executed the next:
- Labored with the working system repository and OS distributors: Google has labored with the working system repository and OS distributors to make sure that the capabilities wanted for confidential computing are a part of their kernels and releases.
- Modified the kernel with silicon distributors: Google has modified the host kernel along with silicon distributors to assist the confidential computing functionality.
- Labored with silicon distributors: Google has labored with each single silicon vendor to grasp the worth of simple to make use of confidential computing and eradicating limitations.
- Contributions to the Confidential Computing Consortium: Google has contributed to consortiums to make sure interoperability between totally different confidential environments of cloud suppliers.
- Labored with different cloud suppliers: Google has labored with different cloud suppliers in addition to silicon distributors resembling Arm and Intel to make sure that they will talk securely and trade information in a verifiable and managed manner.
- Contributed to the open group: Google has contributed to the open group and continues to work overtly to contribute to the function of confidential computing turning into a utility that can be utilized by prospects with none particular necessities.
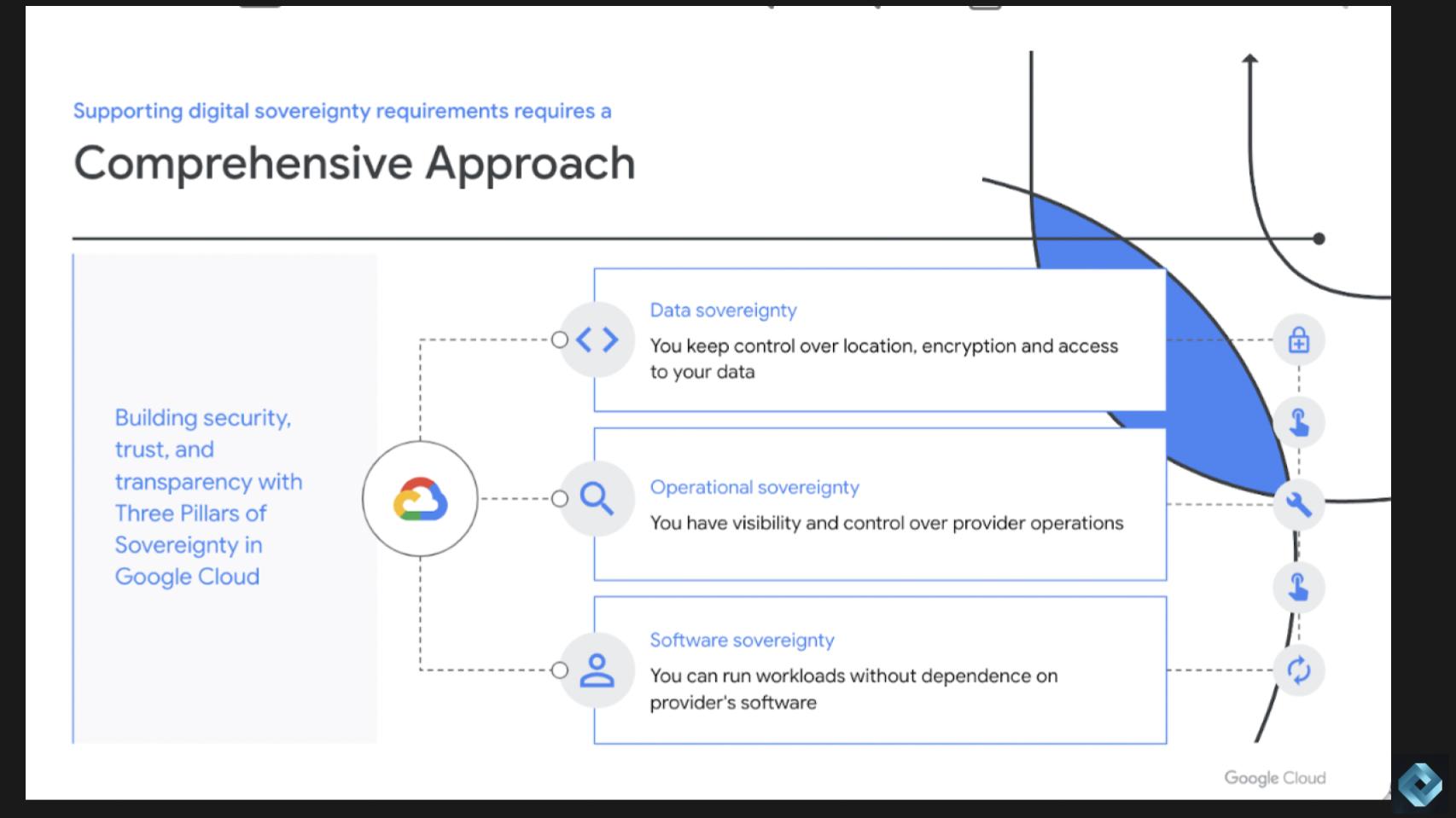
Q: Patricia, How will confidential computing be sure that information sovereignty and that privateness edicts are adhered to? Please clarify Google’s method and the important thing components of this graphic.
In line with Florissi, information sovereignty is just one of many pillars to digital sovereignty. From Google’s perspective, digital sovereignty consists of three pillars: 1) Knowledge sovereignty; 2) operational sovereignty; and three) software program sovereignty.
- Knowledge sovereignty focuses on the situation, encryption, and entry management of the information.
- Operational sovereignty offers full transparency and visibility to Google Cloud prospects over supplier operations.
- Software program sovereignty ensures that prospects can run their workloads with out dependence on supplier software program.
- Confidential computing is on the coronary heart of information safety and ensures the confidentiality, integrity, and availability of the information.
- One other necessary facet of information sovereignty is consumer management, which considerations what occurs to the information when it’s given to another person.
- Confidential computing and coverage enforcement can assure that the information will solely be processed inside a confidential computing atmosphere and that will probably be utilized in accordance with the consumer’s insurance policies.
- Confidential computing is a crucial and important know-how for guaranteeing information sovereignty, particularly with regard to consumer management.
Right here’s a deeper-dive abstract of the dialog:
In line with Florissi, information sovereignty is often involved with two issues: the place the information resides (information residency) and guaranteeing the confidentiality, integrity and availability of the information (information safety). Confidential computing is on the coronary heart of information safety.
Nonetheless, there may be one other facet of information sovereignty that’s usually neglected, which is consumer management. This refers to what occurs to the information when entry is granted to it. Florissi underscores the significance of trusting that the processing of information will abide by the insurance policies set by the consumer.
She additionally notes that there’s a motion in regulation and initiatives, such because the Worldwide Knowledge House Affiliation and GAIA-X, for suppliers and receivers of information to agree on a contract for a way the information will probably be used. The problem is to make sure that the information is used as supposed as soon as it crosses boundaries.
Google’s view is that confidential computing, mixed with coverage enforcement in guaranteeing information sovereignty, notably with regards to consumer management. Coverage enforcement ensures that information is just processed inside the confines of a confidential computing atmosphere, that the workload is verified, and that the information will solely be utilized in accordance with the confidentiality and integrity of the confidential computing atmosphere.
Q: To each. What’s your prediction as to how widespread the adoption of confidential computing will probably be in 2023 and past?
Porter: My prediction in 5, seven years as I said, it’ll change into like a utility. Ten years in the past we couldn’t think about that web sites would have certificates and we might assist encrypted site visitors. Now we do, and it’s change into ubiquitous. It’s precisely the place our confidential computing is headed and heading. I don’t know if we’re there but but. It’ll take a number of years of maturity for us, however we’ll get there.
Florissi: I might double down on that and say sooner or later, within the very close to future, you will be unable to afford not having it [confidential computing]. I imagine as digital sovereignty turns into ever extra prime of thoughts with sovereign states and in addition for multinational organizations and for organizations that need to collaborate with one another, confidential computing will change into the norm. It’ll change into the default mode of operation. For the younger technologists on the market, it’s inconceivable to assume that in some unspecified time in the future in historical past information in transit was not encrypted. And I feel that will probably be inconceivable in some unspecified time in the future within the close to future to have unencrypted information whereas in use.
Watch and listen to Google’s technical experts predict the future of confidential computing.
In abstract
Confidential computing is being touted by the cloud gamers as a promising know-how for enhancing information privateness and safety, however there are additionally those that stay skeptical of its deserves and necessity. The reality most likely lies someplace in between, and it’ll rely upon the precise implementation and the use case as to how efficient confidential computing will probably be. Confidential computing will not be a panacea for all safety challenges, in fact. However the great thing about the tech trade is as a result of there’s a lot competitors confidential computing basically comes at low or no price to prospects. And there’s no apparent draw back.
As with every new know-how, it is very important fastidiously its adoption and make knowledgeable selections based mostly on the precise necessities and constraints of every particular person scenario. However the backside line is: Silicon producers are working with cloud suppliers and different methods firms to incorporate confidential computing into their architectures. Competitors will average worth hikes and, on the finish of the day, this under-the-covers know-how basically will come totally free.
So we’ll gladly take it.
Be in contact
Many because of our friends right this moment Google, Nelly Porter and Dr. Patricia Florissi. Alex Myerson and Ken Shifman are on manufacturing, podcasts and media workflows for Breaking Evaluation. Particular because of Kristen Martin and Cheryl Knight who assist us maintain our group knowledgeable and get the phrase out, and to Rob Hof, our editor in chief at SiliconANGLE.
Keep in mind we publish every week on Wikibon and SiliconANGLE. These episodes are all accessible as podcasts wherever you listen.
E-mail [email protected], DM @dvellante on Twitter and touch upon our LinkedIn posts.
Additionally, take a look at this ETR Tutorial we created, which explains the spending methodology in additional element. Be aware: ETR is a separate firm from Wikibon and SiliconANGLE. If you need to quote or republish any of the corporate’s information, or inquire about its companies, please contact ETR at [email protected].
Right here’s the total video evaluation:
All statements made relating to firms or securities are strictly beliefs, factors of view and opinions held by SiliconANGLE Media, Enterprise Know-how Analysis, different friends on theCUBE and visitor writers. Such statements usually are not suggestions by these people to purchase, promote or maintain any safety. The content material offered doesn’t represent funding recommendation and shouldn’t be used as the premise for any funding choice. You and solely you’re accountable for your funding selections.
Disclosure: Most of the firms cited in Breaking Evaluation are sponsors of theCUBE and/or purchasers of Wikibon. None of those corporations or different firms have any editorial management over or superior viewing of what’s revealed in Breaking Evaluation.
Picture: Alex Mit/Adobe Stock
Present your assist for our mission by becoming a member of our Dice Membership and Dice Occasion Neighborhood of consultants. Be a part of the group that features Amazon Internet Companies and Amazon.com CEO Andy Jassy, Dell Applied sciences founder and CEO Michael Dell, Intel CEO Pat Gelsinger and plenty of extra luminaries and consultants.
Source link