TL;DR: The Cybersecurity and Infrastructure Safety Company (CISA), Nationwide Safety Company (NSA), and the Multi-State Data Sharing and Evaluation Middle (MS-ISAC) issued a joint warning that risk actors (TA) are ramping up a hacking/phishing marketing campaign using reliable distant monitoring and administration (RMM) software program. The CISA notes that it has found a number of assaults inside federal civilian govt department (FCEB) networks.
In September 2022, the CISA carried out audits on a number of FCEB networks and located them to have been sufferer to a “widespread, financially motivated phishing marketing campaign.” A month later, safety researchers at Silent Push reported on a “typosquatting” trojan marketing campaign involving a number of trusted domains, together with PayPal, Microsoft, Geek Squad, and Amazon. On Wednesday, CISA confirmed a number of federal workers members had fallen for the help-desk-themed phishing marketing campaign.
“[We] assess that since at the very least June 2022, cyber felony actors have despatched assist desk-themed phishing emails to FCEB federal workers’s private, and authorities e mail addresses,” the alert reads.
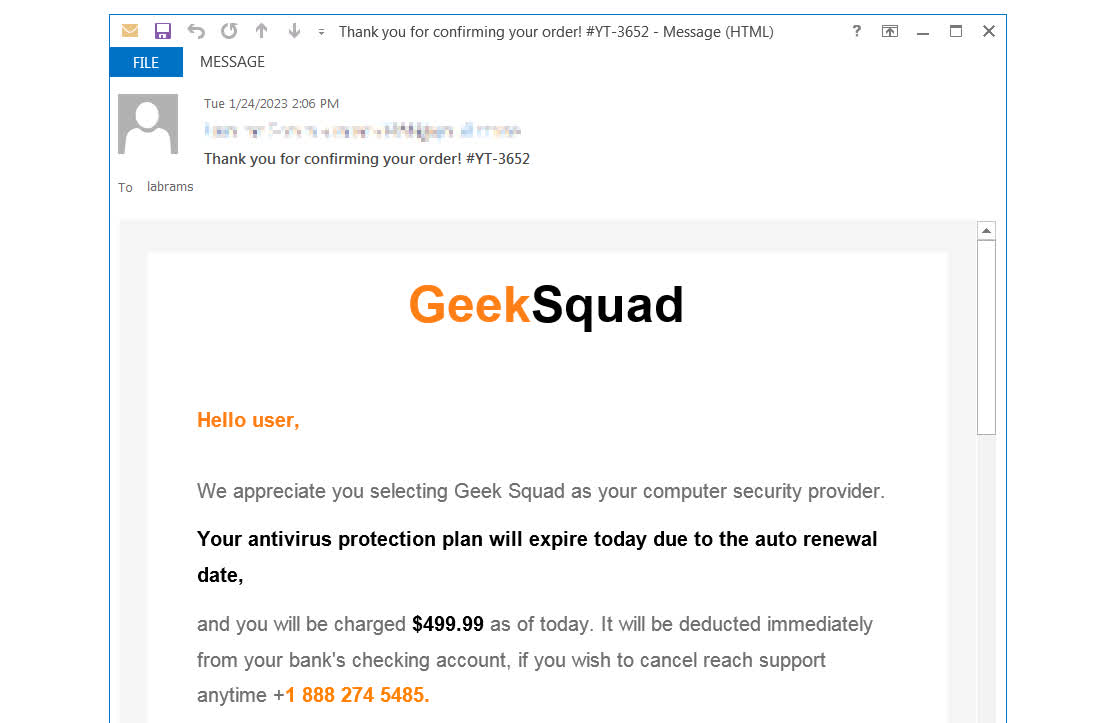
The scams are a bit extra subtle than the everyday phishing emails most individuals ignore. Dubbed “callback phishing,” emails are despatched out that seem reliable, just like the one above from “Geek Squad.” The emails take the type of a high-priced subscription auto-renewal discover and listing a quantity to name to cancel the automated cost or a hyperlink to a “first-stage malicious area.” These are pages that mimic reliable companies like PayPal. The URLs are additionally disguised, for instance, paypalsec.com.
When targets name the quantity or go to the area, they’re satisfied to obtain reliable RMM help-desk software program kind a second stage area, the CISA particularly named ScreenConnect and AnyDesk. The unhealthy actors use moveable executables to bypass safety protections stopping workers from putting in software program. Moveable executables are .exe recordsdata that can run with out being put in on the pc, and most desktop-sharing software program have these.
As soon as the TAs have entry to the goal by the RMM software program, they try to execute a refund rip-off. This assault includes convincing the sufferer to entry their checking account, then altering their account abstract display to make it seem that the corporate refunded an excessive amount of cash. The scammer then asks the goal to cost again the surplus funds.
Combat the fraudsters with hearth.
“The attackers used the distant entry software program to alter the sufferer’s checking account abstract data to indicate that they mistakenly refunded an extra sum of money, then instructed the sufferer to ‘refund’ this extra quantity,” the CISA mentioned.
The discover didn’t listing particular FCEB networks that will have fell sufferer, nor did it point out any damages or monetary losses. It was primarily a warning to make companies conscious and find out how to mitigate their threat. The CISA listing easy preventative administrative measures like blocking phishing emails, auditing distant entry instruments, reviewing logs for RMM execution cases, and different frequent sense safety hygiene. The CISA included an informative, if not considerably cringe, infographic for these .
Source link


