In a nutshell: Safety researchers at ThreatFabric have uncovered an Android banking-app malware referred to as “Hook.” This system permits hackers to take over a goal’s telephone remotely. Unhealthy actors can use it to steal knowledge, exfiltrate personally identifiable data (PII), make monetary transactions, and extra.
A menace actor (TA), going by DukeEugene, sells the malware on the darkish internet and claims that he wrote the code “from scratch.” Nevertheless, TreatFabric’s code analysis reveals it to be a fork of Ermac, probably the most detected malware households within the wild. Whereas many of the code is from the well-known banking trojan, the remainder is bits and components of different packages, exhibiting there isn’t a honor amongst thieves.
Regardless of DukeEugene’s false claims of authorship (though the TA did write the unique Ermac code), Hook brings many new options to the malware household. It consists of WebSocket communication and encrypts its site visitors utilizing an AES-256-CBC hardcoded key.
What units Hook other than Ermac is its capability to make use of digital community computing (VNC) to hijack an Android telephone. The software program can ship digital swipe gestures, scroll, take screenshots, and simulate keypresses, together with an extended press.
“With this characteristic, Hook joins the ranks of malware households which might be capable of carry out full DTO [device take-over] and full a full fraud chain, from PII exfiltration to transaction, with all of the intermediate steps, with out the necessity of extra channels,” stated ThreatFabric. “This sort of operation is far more durable to detect by fraud scoring engines and is the principle promoting level for Android bankers.”
The researchers say that Hook additionally acts as a file supervisor. Hackers can use it to view all information on the telephone or obtain any they discover priceless. It might probably additionally view or obtain any photos on the telephone. Hook does not even want to make use of shell instructions to carry out file exfiltration. As an alternative, it makes use of present Android APIs to steal the information. This functionality coupled with its entry to real-time GPS monitoring data makes it a dual-duty banking-trojan/adware suite.
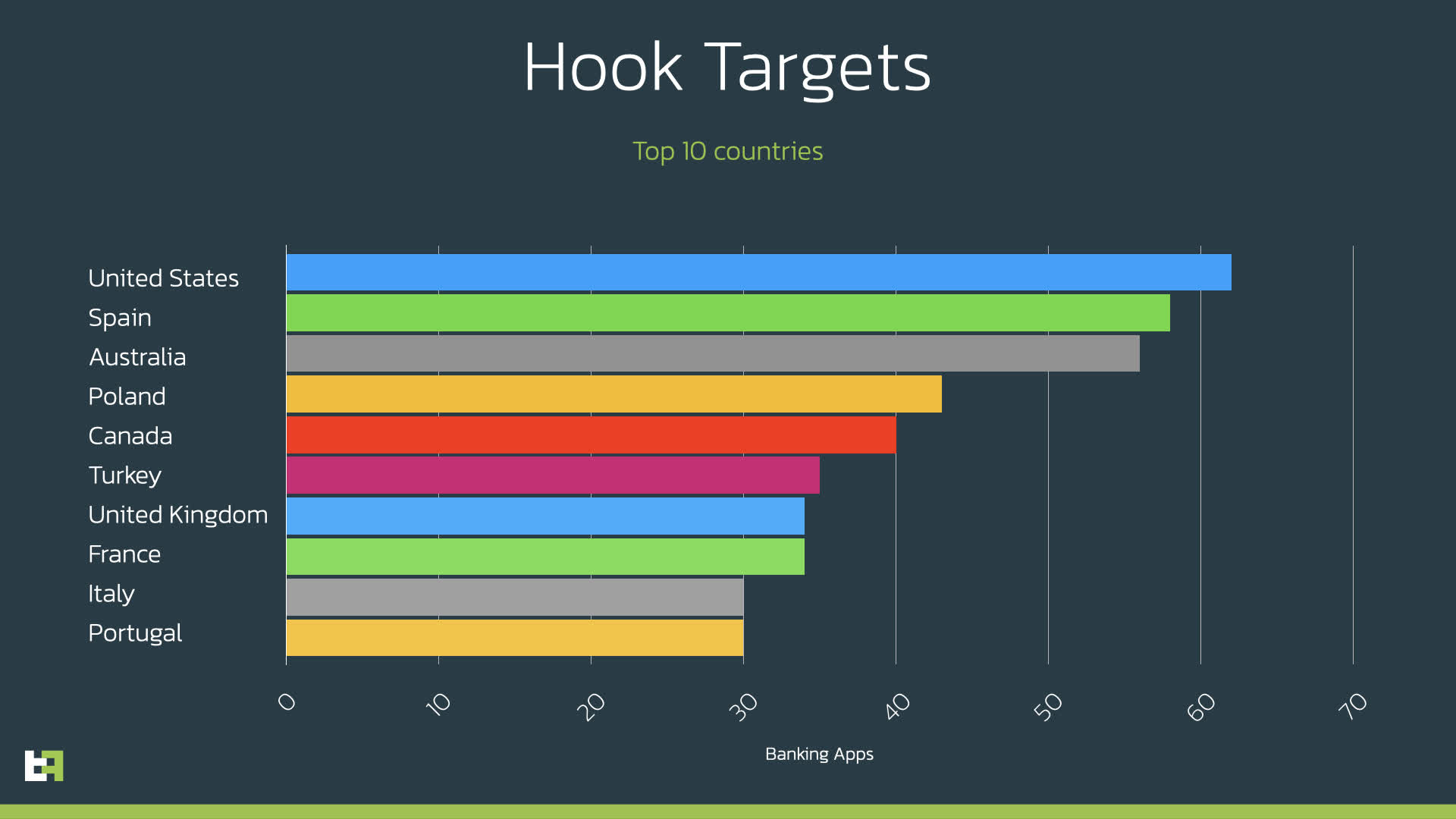
The malware’s victims (banking apps) are widespread and in depth, with the US, Australia, Canada, the UK, and France all reported within the high ten of targets. Nevertheless, ThreatFabric says that the checklist of nations exterior the highest ten is wide-sweeping, with these areas solely barely decrease than tenth place. The researchers posted a whole checklist of focused apps and the package deal names related to Hook on the finish of their blog post. The article additionally has all of the technical nuts and bolts for these .
As to mitigation, at all times follow protected safety hygiene. Keep away from downloading software program exterior of the Google Play Retailer or different trusted sources. Additionally, Hook asks for Accessibility permissions to realize admin privileges, so be cautious of apps asking for that kind of entry.
Picture credit score: ThreatFabric
Source link


