A newly disclosed vulnerability in Apple Inc.’s Safari web browser and related WebKit code can leak a users’ identity and website history.
Discovered by researchers at FingerprintJs Inc., the vulnerability relates to Safari 15’s implementation of the IndexedDB application programming interface. IndexedDB is a browser API for client-side storage designed to hold significant amounts of data and is found in many browsers.
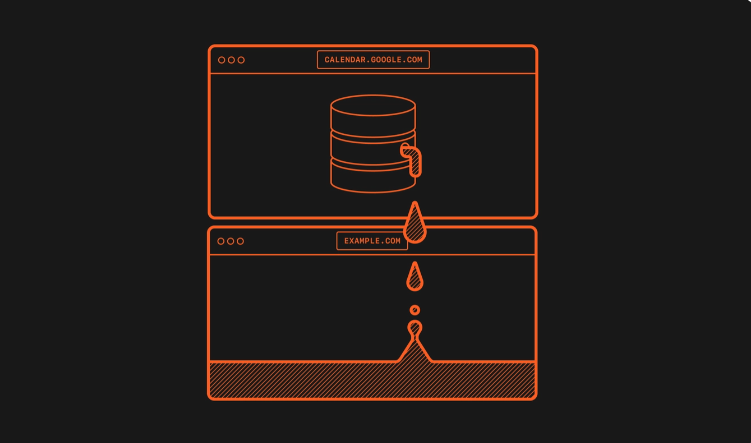
The problem with Safari is the way it has been implemented by Apple, violating the “same-origin” policy that prevents documents and scripts in one location from interacting with content from another. As such, a malicious website could find Google LLC account information and well has history from open tabs and windows.
The issue doesn’t affect the data within the IndexedDB but exposes the names of the databases. In some cases, the researchers found websites that use unique user-specific identifiers in database names. This means that authenticated users can be uniquely and precisely identified, with some popular examples including YouTube, Google Calendar and Google Keep.
“The Google User ID is an internal identifier generated by Google,” the researchers explain. “It uniquely identifies a single Google account. It can be used with Google APIs to fetch the public personal information of the account owner. The information exposed by these APIs is controlled by many factors. In general, at minimum, the user’s profile picture is typically available.”
They add that what this means is that an untrusted or malicious website can learn a user’s identity and link together multiple separate accounts used by the same users.
FingerprintJS has created a demo page that shows how the user’s identity is leaked if they are logged into their Google account in the same browser. The demo detects the presence of 20+ websites in other browser tabs or windows, including Google Calendar, Youtube, Twitter, and Bloomberg.
The vulnerability was disclosed to Apple and the WebKit Bug Tracker in late November but has only been fixed as of this morning, Jan. 17. The researchers add that the bug continues to persist for end-users until the patch has been released.
Image: FingerprintJS
Show your support for our mission by joining our Cube Club and Cube Event Community of experts. Join the community that includes Amazon Web Services and Amazon.com CEO Andy Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger and many more luminaries and experts.
Source link