September 17, 2025
How do mailbox suppliers like Gmail and Yahoo know you’re who you say you’re? When an e mail arrives at a receiving mail server, what helps them work out for those who’re a spammer, a scammer, or a authentic sender? E mail authentication protocols are the reply.
E mail fraud is an enormous drawback, particularly in the case of points like email spoofing. Defending the security of e mail recipients is necessary to mailbox suppliers and it ought to matter to you as an e mail sender too.
E mail entrepreneurs such as you need subscribers to belief that campaigns are secure to open, and also you need the e-mail channel to proceed being a spot the place manufacturers and clients can join. As of 2024, all senders might want to have e mail authentication protocols in place in the event that they wish to attain individuals utilizing main services like Gmail, Yahoo Mail and Outlook.
However once you begin listening to about protocols like SPF, DKIM, DMARC, and BIMI, to not point out different acronyms like SMTP and MTAs, it might really feel such as you’re wading via a bowl of alphabet soup. Don’t fear. This information will shed some gentle on what you could know and level you within the path of the right way to arrange e mail authentication protocols appropriately.
E mail authentication protocols are unsung heroes working behind the scenes to confirm that senders are who they declare to be earlier than emails attain inboxes. Implementing these verification strategies not solely reveals accountability but in addition improves email deliverability.
The protocols can get fairly technical, and all of the acronyms
may remind you of a bowl of Alpha-Bits cereal. However let’s begin by exploring
the fundamentals.
What’s e mail authentication?
E mail authentication is the method of utilizing a number of
strategies to make sure that messages will not be faked or solid earlier than they get
delivered. Mail servers on the receiving finish use e mail authentication protocols
to confirm the sender title within the “from” discipline and different info positioned in
the e-mail header.
These protocols additionally examine to ensure emails weren’t altered in transit, they usually inform mail servers what to do with messages that fail authentication.
E mail authentication protocols defend us from spam and phishing makes an attempt, particularly a kind of phishing often called e mail spoofing. Right here’s a fast rationalization of the principle protocols and specs related to e mail authentication:
- Sender Coverage Framework (SPF): An inventory of sources which might be authorized to ship mail on behalf of your area.
- DomainKeys Recognized Mail (DKIM): A mixture of public and encrypted keys used to confirm the identification of a sender earlier than a receiving mail server accepts a message for supply.
- Area-based Message Authentication, Reporting and Conformance (DMARC): A specification that checks for SPF and DMARC alignment earlier than informing receiving mail servers the right way to deal with failures. DMARC additionally gives stories on e mail visitors to senders.
- Model Indicators for Message Identification (BIMI): An e mail specification that permits senders to have a verified brand displayed on the inbox degree when they’re implementing DMARC.
All these e mail authentication protocols and specs are DNS TXT information that mailbox suppliers and receiving mails servers confer with when deciding whether or not to simply accept your message for supply and whether or not it ought to be filtered into spam or attain the inboxes of their customers.
E mail authentication protocol necessities in 2025
When Gmail and Yahoo announced new requirements for bulk senders that started rolling out final yr, followed by Microsoft in 2025, the largest change of all was about utilizing e mail authentication protocols.
For a very long time, SPF, DKIM, and DMARC had been strongly beneficial however not required. That’s not the case any extra. In 2025, all senders should be utilizing some type of e mail authentication. If you’re a bulk sender – which usually means sending hundreds of emails day by day – then you could be utilizing all three of those authentication strategies.
However even for those who’re not a bulk sender, implementing SPF, DKIM, and DMARC is a great transfer. Mailbox suppliers are getting critical about stopping issues like spoofing and slicing down on spam.
When Sinch Mailgun surveyed senders for its unique report, The state of email deliverability 2023, outcomes confirmed a good portion of senders weren’t utilizing SPF, DKIM, and DMARC, whereas many others had been unsure of how their emails had been being authenticated:
- Utilizing SPF?
- Sure: 55.4%
- No: 12.8%
- Not sure: 31.8%
- Utilizing DKIM?
- Sure: 58.5%
- No: 11.1%
- Not sure: 30.4%
- Utilizing DMARC?
- Sure: 42.5%
- No: 18.7%
- Not sure: 38.8%
These findings counsel there are numerous senders who want to enhance e mail authentication – or no less than examine to ensure it’s arrange. In some instances, your e mail service supplier (ESP) could also be authenticating your emails.
For extra on what this implies, we suggest watching a webinar from our colleagues at Sinch Mailgun. They hosted representatives from each Google and Yahoo to get solutions about what senders can anticipate and what it is best to do to satisfy the necessities. Marcel Becker of Yahoo informed webinar attendees that the brand new necessities are actually about ensuring senders do the issues they need to already be doing.
All of those necessities have been nicely documented finest practices for years. Lots of senders have already carried out them. Authenticating your e mail visitors ought to be one thing that you just’re already doing for those who care in regards to the well being of your e mail visitors in addition to your infrastructure.
Marcel Becker
Senior Director of Product at Yahoo
What’s e mail spoofing?
E mail spoofing includes messages that look like from a identified or dependable sender, however they’re truly an try to amass delicate knowledge resembling entry to an individual’s funds or on-line accounts. E mail spoofing results in a pretend web site with a bogus login web page the place targets are requested to enter credentials or different info.
These e mail phishing makes an attempt usually attempt to forge the sender
title in addition to imitate the look of emails from recognizable manufacturers together with
monetary establishments, social media websites, or on-line retailers like
Amazon.com.
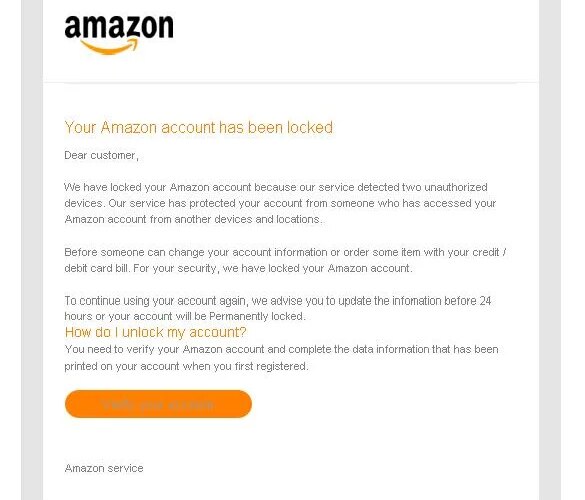
Amazon spoofing is so widespread the corporate has its personal e mail handle for reporting potential scams and suspicious communications.
Instance of an Amazon e mail spoof


Even savvy web customers could be tricked with e mail
spoofing. Intelligent scammers usually prey on the concern of getting hacked to trick
individuals. That’s why e mail authentication protocols are so useful. They hold
malicious messages from ever reaching the inbox.
How does e mail authentication work?
E mail authentication includes a number of attainable strategies of
validating the origin of an e mail and area possession of message switch
brokers (MTAs) that had been concerned in transferring or modifying an e mail.
Put merely, emails are despatched from a sure area or subdomain. E mail authentication protocols are guidelines positioned in DNS (area title system) information for these sending domains. To authenticate an e mail, the sending mail server and receiving mail server speak to one another, double-checking protocols within the DNS for affirmation of the sender’s identification.
Whereas every protocol is exclusive, it usually works like this:
- The sender/area proprietor establishes guidelines for authenticating emails despatched from or on behalf of its domains.
- The sender configures sending e mail servers and publishes the foundations within the DNS information.
- Mail servers that obtain emails authenticate messages from the sender utilizing the revealed guidelines.
- Receiving e mail servers then observe the revealed guidelines and both ship, quarantine, or reject the message.
Along with verifying authentic senders, e mail authentication protocols additionally assist set up IP handle and area status in order that malicious senders could be extra simply recognized.
The 4 pillars of e mail authentication
Easy Mail Switch Protocol (SMTP) is the usual basis upon which e mail is constructed. It’s what’s used to ship and obtain messages. Nonetheless, SMTP doesn’t embrace a option to validate a sender’s identification, which is what makes it inclined to spammers and phishing.
E mail authentication protocols emerged within the early 2000s as a option to improve the safety of SMTP and thwart the rise of e mail spam. SPF and DKIM had been the primary extensively adopted strategies. DMARC quickly adopted as a coverage to verify and prolong SPF and DKIM. BIMI is the brand new e mail specifcation on the block.
These e mail authentication protocols present a standardized means for companies resembling Gmail, Outlook, Yahoo, and Apple Mail to confirm the identification of senders versus utilizing separate, proprietary strategies to authenticate e mail.
So, whereas e mail authentication might sound sophisticated,
technical, and even a bit messy … these protocols do present some
standardization. E mail entrepreneurs ought to be glad we don’t should observe
totally different protocols for each mailbox supplier.
Let’s take a more in-depth have a look at SPF, DKIM, DMARC, and BIMI.
1. SPF (Sender Coverage Framework)
The Sender Coverage Framework, or SPF, is an e mail authentication
protocol that gives a DNS document specifying which IP addresses or hostnames
are approved to ship e mail from a site.
SPF is a DNS TXT entry that permits the receiving mail server to examine that an e mail claiming to return from a sure area is related to a licensed IP handle. The receiving server does this by wanting up guidelines for the bounce or return-path area within the DNS document. That’s in comparison with the foundations within the SPF document to make sure there’s a match.
With out implementing SPF, mailbox suppliers are more likely to mark messages as spam.


In some instances, e mail service suppliers (ESPs) deal with SPF
implementation routinely. That’s as a result of the ESP could present the IP handle
and the return path. Nonetheless, for those who ship a excessive quantity of e mail, you probably
wish to keep away from utilizing a shared IP handle. A devoted IP helps you management
sender status. Remember that in case you are on a shared IP handle, your
SPF document could must be up to date once you change ESPs.
One of many downsides of SPF is that it gained’t work when
emails are forwarded. In case your model is one which depends closely on e mail
word-of-mouth (getting your viewers to ahead your message), there’s an honest
probability of the SPF failing validation and by no means reaching anybody past your
checklist.
2. DKIM (DomainKeys Recognized Mail)
The subsequent e mail authentication protocol is the results of two
strategies developed to forestall e mail forgery. In 2004, Yahoo merged its
“DomainKeys” with Cisco’s “Recognized Web Mail.”
DomainKeys Identified Mail,
or DKIM, makes use of an encrypted key often called a digital signature. This signature is
added to e mail headers to assist confirm a sender and affiliate a message with a
particular area. DKIM additionally must be arrange inside a sender’s DNS document.
You may consider DKIM like a watermark or fingerprint that
is exclusive to an e mail sender. In contrast to SPF, DKIM signatures proceed working when
an e mail is forwarded.
There are literally two keys that make DKIM work. Directors
generate a public key on the DNS document in addition to a personal key that mail
servers transporting the e-mail to the recipient use to confirm authenticity. The
non-public secret’s the DKIM signature within the e mail header.
The digital signature lets the MTA or receiving mail server know the place info on the general public key could be retrieved for authentication of the e-mail. Lastly, the general public secret’s used to confirm the encrypted key within the DKIM signature. This reveals a connection between the e-mail and the sending area the place the general public secret’s positioned.


As safe as all of this sounds, it’s nonetheless attainable for hackers to come up with DKIM keys and use them to impersonate a sender. For that purpose, it’s beneficial that DKIM keys are modified a number of occasions per yr.
In keeping with a 2015 article on CircleID.com, some ESPs could share DKIM signatures amongst clients. That’s no good as a result of a compromised digital signature may influence a bunch of corporations without delay. Hopefully, this subject is not as widespread because the article states. However, in case your ESP is offering your DKIM signature, it’s a query that’s price asking.
If you could produce your personal digital signature, there are DKIM mills that assist create these e mail authentication information for you. You may also be taught more about DKIM signatures and see an instance document right here on our weblog.
3. DMARC (Area-based Message Authentication, Reporting, and Conformance)
It was truly PayPal that led a bunch in growing DMARC
expertise to enhance upon present e mail authentication strategies. PayPal was
(and is) generally impersonated by cybercriminals utilizing pretend emails. A number of
different massive manufacturers in addition to main mailbox suppliers instantly adopted the
technique.
Technically, DMARC isn’t an e mail authentication protocol so
a lot as a coverage that mail servers on the receiving finish confer with earlier than
delivering an e mail. DMARC helps decide the right way to deal with a message when it
fails authentication.
This coverage, also called Domain-based Message Authentication, Reporting, and Conformance, is yet one more document that’s revealed within the DNS. It specifies whether or not a sending area is utilizing SPF, DKIM, or each protocols for authentication. DMARC is commonly described as a option to get one of the best out of SPF and DKIM as a result of it creates a typical framework utilizing each protocols
For many individuals, lacking an necessary, authentic e mail is
even worse than letting spam get via to their inbox. Actual emails can
generally fail DKIM and SPF authentication for varied causes. So, mailbox
suppliers could let emails via in the event that they don’t go the check however seem to return
from a legit sending area. DMARC makes it extra clear what to do.
A DMARC coverage permits senders to create a framework that defines its e mail authentication strategies and dictates the right way to deal with messages that violate the coverage. There are three choices area homeowners can select to specify the therapy of emails that fail DMARC validation:
The three DMARC p= insurance policies:
- p=none: Take no motion. Deal with the e-mail
as if there have been no DMARC validation. This coverage additionally helps acquire an
understanding of the e-mail stream with out impacting movement. - p=quarantine: Settle for the e-mail however ship
it to a junk or spam folder as an alternative of the principle inbox. Or, isolate the
suspicious message for additional inspection. - p=reject: Cease supply of the e-mail to
any folder. The sender can be knowledgeable why the e-mail will not be getting delivered.
A DMARC coverage that rejects unvalidated emails is the strongest, however it might imply e mail from a site stops flowing if for some purpose SPF and DKIM are failing.


A advantage of implementing a DMARC coverage is that senders get
common DMARC stories, which offer the next info:
- Which servers and third events are sending mail
to your specified area. - The proportion of emails that go DMARC.
- What servers or third events are sending emails
that failed DMARC. - What actions receiving mail servers tackle
unauthenticated emails.
DMARC nonetheless isn’t good. Like SPF, it might break throughout e mail forwarding. DMARC may additionally be troublesome for senders to arrange, and considerations over stopping the movement of authentic emails discourage stringent insurance policies.
Nonetheless, in case your group manages to arrange and implement a profitable DMARC coverage, you’ll have an efficient option to cease most phishing emails that try and spoof your sending area.
DMARC coverage necessities in 2025
Gmail, Yahoo, and Microsoft’s new necessities for bulk senders require using DMARC together with SPF and DKIM. Nonetheless, it’s acceptable to have a DMARC coverage of p=none – no less than for now.
The mailbox suppliers have indicated that that is simply step one in the direction of requiring an enforced DMARC coverage of both p=reject or p=quarantine. First, they need extra organizations to undertake DMARC. As soon as the requirement is established, they’ll take issues a step additional and a p=none coverage gained’t reduce it anymore.
To be clear… a DMARC coverage of p=none is not the requirement. It’s the minimal allowed at this cut-off date. As Marcel Becker of Yahoo told senders, implementing DMARC is a win-win-win state of affairs for mailbox suppliers, senders, and e mail recipients.
The top aim is ideally a coverage of p=reject. That’s what DMARC is for. Guaranteeing that your area can’t be spoofed and defending our mutual clients from abuse.
Marcel Becker
Senior Director of Product at Yahoo
4. BIMI (Model Indicators for Message Identification)
BIMI is the most recent member of the e-mail authentication household. Gmail, Yahoo, and Microsoft will not be requiring senders to implement BIMI. That’s as a result of this specification is supposed to encourage organizations to undertake all the opposite e mail authentication protocols. It’s virtually like a reward for having robust authentication strategies.
In contrast to the opposite specs, BIMI leads to one thing your subscribers can see of their inbox. When carried out appropriately, BIMI shows a verified, trademarked, brand-designated brand subsequent to messages within the inbox.
The BIMI brand reveals an e mail could be trusted as a result of it means different e mail authentication strategies are in place. It gives subscribers with a sign that an e mail is certainly genuine. This provides an extra degree of belief as a result of, even when scammers handle to get a phishing e mail delivered, it gained’t show a brand.


As a way to get mailbox suppliers to show a BIMI brand,
you will need to have a completely functioning DMARC coverage in place with SPF and DKIM
information arrange. In some methods, BIMI is the payoff for pursuing the opposite e mail
authentication strategies.
Like the opposite protocols, BIMI is a TXT document tied to a
area’s DNS. However, earlier than you place a BIMI document in place, you could have a correctly
formatted brand.
Suitable BIMI logos are SVG information within the form of an ideal sq., which could be cropped right into a circle. They require a stable background and ought to be revealed by way of HTTPS. BIMI brand information must be small and shouldn’t exceed 32kb. Lastly, your brand should even be a registered trademark to satisfy requirements.
Google launched a Gmail pilot program for BIMI in 2020. In July of 2021, information broke that Gmail was officially rolling out full support for BIMI. In 2023, Apple introduced that it will additionally help BIMI logos in its Apple Mail consumer beginning with iOS 16. That’s massive information as a result of it’s probably {that a} sizable portion of your checklist are utilizing both Gmail or Apple Mail. It actually makes the effort and time of establishing e mail authentication protocols appear much more worthwhile.
Implementing BIMI ought to finally improve subscriber confidence within the supply of your emails. Get extra recommendation, assets, and instruments at BIMIGroup.org. You may also hear from two BIMI Group consultants in our AMA on Brand Indicators for Message Identification.
Must you use all e mail authentication protocols?
Brief reply? Sure.
You understand how they are saying, “two heads are higher than one”? That’s like utilizing each SPF and DKIM. You understand how College Home Rock and Blind Melon say, “three is the magic number”? That’s like including DMARC to the e-mail authentication combine.
And as talked about, you’ll want DMARC to get probably the most out of each these protocols and to get a BIMI brand to show.
Whereas it may actually take effort and time, establishing
robust e mail authentication strategies is price it, particularly you probably have the
assets.
E mail entrepreneurs shouldn’t should deal with e mail authentication protocols alone. You’ll almost definitely have to get your IT workforce or somebody esle with technical experience that can assist you arrange in DNS information. Your ESP may additionally have to get entangled. Colleagues, distributors, or safety consultants ought to find a way that can assist you troubleshoot points as you’re employed to verify that e mail authentication protocols are working appropriately.
Who ought to take e mail spoofing critically?
Whether or not or not you prioritize e mail authentication depends upon how necessary safety is to your model – and extra importantly – your clients.
For main on-line retailers, monetary establishments, client
tech corporations, and others coping with delicate private and enterprise
info, e mail spoofing generally is a massive drawback.
Microsoft repeatedly tops a quarterly report from Check Point, a cybersecurity agency that lists the manufacturers most frequently spoofed in phishing makes an attempt. Different regulars on the phishing manufacturers checklist embrace main banks like Wells Fargo and Chase. PayPal and Dropbox usually make the checklist as do social websites like LinkedIn, Instagram, and Fb. E mail spoofing even targets youngsters utilizing the net recreation Roblox.
Nonetheless, you don’t should be a big firm to get spoofed by scammers. An article from Kelly Sheridan on Dark Reading says criminals are actually utilizing smaller manufacturers for e mail spoofing. Actually, that consists of Test Level, the cybersecurity firm that publishes the model spoofing checklist. Sheridan writes:
Many [smaller companies] don’t have assets to detect fraudulent web sites; in consequence, a spoofed website might be up for days or even weeks earlier than the model proprietor takes it down … It’s incentive for attackers to keep away from massive manufacturers with extra subtle defenses.
The Federal Trade Commission (FTC) has extra information on what to do if your enterprise is spoofed.
The advantages of utilizing e mail authentication protocols
In the event you’re on the fence about e mail authentication protocols,
otherwise you want a option to persuade others in your group that it’s price
implementing, listed below are the important thing benefits:
1. Defend your clients and subscribers
It will not be your direct accountability to cease e mail
spoofing from fooling individuals, and it’s unlikely you’d be held chargeable for a
buyer who will get scammed. Nonetheless, the truth that e mail entrepreneurs can do
one thing means we should always.
Though a phishing rip-off isn’t your fault, that won’t
be how your clients understand it. Definitely, clients who’re scammed by
e mail spoofing of your model may develop into very hesitant to open and have interaction with
authentic emails from you. Which ends up in the subsequent profit …
2. Defend your model status
In a world the place everybody faces cybersecurity threats day by day, manufacturers which have a status for being secure and safe are trusted.
Phishing emails exploit belief in your model. In the event you can cease
these malicious messages from reaching inboxes, you’re additionally stopping the
erosion of belief. E mail authentication protocols are instruments you need to use to cease
phishing and defend your model’s status.
Talking of status, e mail authentication additionally helps you
set up a robust sender status. That leads us to learn quantity three …
3. Assist e mail deliverability
E mail authentication can have a direct influence on inbox placement. When mailbox suppliers can verify the supply of an e mail and the identification of the sender, it may be confidently delivered to inboxes.
However, failure to implement e mail authentication protocols will increase the probability of authentic communications touchdown in spam or getting rejected by mailbox suppliers. E mail authentication is without doubt one of the best methods entrepreneurs can help e mail deliverability and a great sender status.
Handle e mail deliverability with Mailgun Optimize
E mail authentication protocols are only one side of the advanced and nuanced practices related to deliverability. However reaching inbox placement doesn’t should be a complete thriller. With the best accomplice, you’ll be able to acquire the visibility you could keep away from spam, keep off e mail blocklists, and keep a great sender status with mailbox suppliers.
Mailgun Optimize is a whole e mail deliverability suite. Right here’s simply a few of what it might do:
- Reputation Monitoring: This function screens blocklists whereas serving to you keep away from spam traps. It integrates with each Google Postmaster Instruments and Microsoft SNDS so you’ll be able to control your sender status with these necessary suppliers.
- Inbox Placement Reports: This answer gives reporting that allows you to know the place emails are prone to land – earlier than you hit ship. You may also use this function to make sure your e mail authentication protocols are correctly configured.
- Email Validation: Confirm each contact in your database or arrange e mail verification on enroll varieties to take care of good checklist hygiene.
Whereas e mail authentication can get technical, there’s no denying the actual fact it’s definitely worth the effort and time to get issues working. Now that Gmail and Yahoo are requiring authentication, there’s no excuse. Be sure you know if and the way your messages are authenticated in 2024.
Source link