Emails are usually not only a communication medium but in addition a vital channel for advertising and marketing. A Statista report signifies that the overall variety of email users will surge to 4.6 billion by 2025. Subsequently, there is no such thing as a denying the truth that not solely is e mail advertising and marketing profitable, but in addition a vital a part of your campaigns to draw audiences.
E-mail advertising and marketing has benefits like personalised communications, higher interplay, and buyer relationships. Nevertheless, e mail safety is an enormous concern for a lot of organizations. E-mail advertising and marketing campaigns will be the topic of cyberattacks, together with malware assaults, phishing, spam, and extra.
We are going to talk about various kinds of cyber threats that you could be encounter to your e mail advertising and marketing campaigns and e mail safety greatest practices. Allow us to first perceive what e mail safety is!
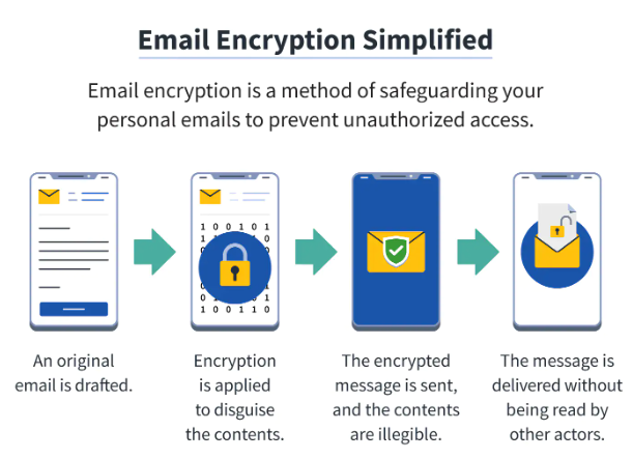
E-mail safety encompasses completely different approaches and applied sciences that you need to use to proctor e mail communications from unauthorized entry, knowledge breaches, and different cyber threats. It might embrace safety measures like encryptions, consumer authentications, spam filters, firewalls, and protocols.
Encryptions assist safe e mail content material. On the similar time, implementing authentication protocols can assist you establish the sender and receiver of the e-mail message. As well as, antispam software program permits safety towards malicious emails.
Nevertheless, greater than implementing safety protocols and software program is required, as you have to practice staff to be vigilant towards social engineering practices.
One advantageous instance is to make sure that you practice staff to keep away from opening emails from unknown sources.
Suppose you’re providing buyer companies by means of emails. Educating customers on cyber threats of doxing and password administration is important. Hackers leverage social engineering practices to entry consumer credentials and collect private knowledge. Additional, they threaten customers of constructing the information public for extortion or ransom.
So, it turns into essential for companies to enhance e mail safety to make sure there aren’t any incidences of doxing.
First, e mail safety is crucial to defending your organization’s delicate knowledge. Primarily, your e mail system wants particular insurance policies to guard very important knowledge towards unauthorized entry, manipulation, and interception.
Executives at prime designations in your enterprise usually ship delicate info for various enterprise actions. For instance, a knowledge analyst might share very important customer data with the gross sales group by means of e mail. E-mail safety protocols make sure that malicious actors don’t achieve entry to consumer knowledge avoiding any harm to your enterprise.
Establishing the e-mail safety protocol is one key facet of knowledge safety. Nevertheless, there are e mail safety practices that shield your methods towards completely different cyber threats.
Such e mail safety practices can embrace:
- Commonly evaluate your e mail system for suspicious exercise like phishing.
- Updating your e mail software program and signatures to guard towards spoofing assaults,
- Guaranteeing that customers have robust passwords and encryption keys for his or her emails,
- Configuring your e mail system to ship notifications whether it is compromised or if messages are stolen
- Pre-define e mail safety protocols and implement them on an organizational degree to make sure higher knowledge safety.
- Educate your employees on e mail safety.
If you wish to outline safety protocols, establish the threats, analyze the vulnerabilities and put together methods to safe emails turns into essential.
The most typical e mail advertising and marketing threats embrace spam, phishing assaults, malware, and extra. For instance, hackers can steal your id and use it to join an account with a e-newsletter mailing checklist to obtain unsolicited emails and business firm gives. Cyber attackers also can entry your mailbox and ship out undesirable mailings in your behalf with out consent.
#1. Spam
E-mail spam is the principle risk to e mail advertising and marketing success, accounting for over 60% of all complaints about email marketing. It may be intrusive, annoying, and even offensive. Spammers ship bulk emails with out consent or permission from the recipients to abuse e mail entrepreneurs.
Cyber-attackers can steal e mail addresses and use them to ship spam emails to customers. Additional, they use bulk emails to discredit entrepreneurs and harm their reputations. One of the best ways to fight spam emails is to make sure your content material is efficacious and related.
Make your messages clear and concise. Additional, use opt-in forms in your e mail advertising and marketing campaigns wherever attainable. Additionally, hold observe of whom you’re sending mail to for higher identification of the recipient.
#2. Phishing
E-mail phishing is a web-based fraud the place an attacker makes use of faux e mail addresses to execute social engineering practices. For instance, cyber attackers make it appear like an e mail from a corporation’s advertising and marketing or gross sales group. Utilizing faux e mail, they trick the recipient into offering delicate info, corresponding to passwords or bank card numbers.
Attackers additionally use e mail to direct the recipient to a faux web site that appears legit to gather private info. E-mail phishing goals to achieve entry to delicate info that can be utilized for fraudulent actions.
#3. Malware
Malware is a cyber risk delivered by means of e mail attachments. Attackers disguise malicious attachments by means of file codecs like PDFs, e-files, paperwork, and others. Disguising the attachments is crucial to executing social engineering practices.
In different phrases, customers open particular attachments connected to the e-mail, injecting malicious scripts into the gadget. It might have an effect on email-marketing campaigns by exposing delicate info of customers.
#4. Spoofing
E-mail spoofing is a cyberattack that targets companies utilizing emails with solid sender addresses. As a result of the recipient trusts the alleged sender, they’re likelier to open the e-mail and work together with its contents, corresponding to a malicious hyperlink or attachment. Attackers act as a marketer and ship malicious emails with attachments to clients. Clients who obtain emails by means of legit e mail IDs or these resembling them might present delicate info that hackers expose.
#5. Botnet messages
A botnet is a gaggle of contaminated computer systems managed by a single consumer or hacker. These gadgets can be utilized for spamming, sending viruses, and different assaults. One in all e mail’s most vital threats is spam. Spammers can use botnets to ship giant quantities of unsolicited emails, damaging your enterprise’s fame and credibility.
Botnet-infected machines can be utilized to unfold viruses extra simply, they usually can assist hackers steal info or achieve entry to networks. Nobody is aware of what number of botnets are on the market, however authorities consider tens of thousands and thousands of contaminated computer systems exist at any given time.
#6. BEC (Enterprise E-mail Compromise)
BEC (Enterprise E-mail Compromise) is an e mail risk the place a hacker good points entry to company e mail accounts by utilizing stolen credentials. As soon as contained in the account, they’ll learn and doubtlessly modify emails despatched from that account and extract delicate info like login particulars and buyer knowledge.
Now that you’re acquainted with completely different cyber threats that may have an effect on your e mail advertising and marketing marketing campaign, listed below are a few of the greatest practices to observe.
E-mail advertising and marketing is all about communication; securing your e mail campaigns can imply every part to your enterprise. From encryptions to multi-factor authentications, many various greatest practices exist, however we are going to handle 11 efficient greatest e mail safety practices.
1. Encrypt advertising and marketing emails
Encrypting your emails utilizing an encryption algorithm like PGP or S/MIME will shield them from being intercepted by hackers. To take this one step additional, encrypt your e mail with stable encryption applied sciences, corresponding to AES-256 or SHA-2 hashing algorithm. This may shield your emails from being accessed by unauthorized people.
A strong assault that e mail methods face is a man-in-the-middle (MITM) assault. Encryption is a technique to make sure that your e mail content material is safe from such assaults. It protects e mail content material from cyber-attackers by conserving the information nameless in the course of the transit between the recipient and the sender.
Nevertheless, if you happen to plan to safe emails for advertising and marketing campaigns, an Extended Validation (EV) SSL certificate is right. It is likely one of the most vital e mail safety greatest practices for phishing assaults, because the delicate content material of e mail stays safe. EV SSL certificate comes with a multi-domain characteristic that gives the best authentication of a enterprise.
In case you are an enterprise, consumer belief turns into essential. Certificates Authority (CA) verifies all of your organizational particulars earlier than issuing the EV certificates. Subsequently, customers can belief your model earlier than interacting along with your emails or some other content material.
2. Use e mail safety software program
Make the most of e mail safety software program to guard your Gmail, Outlook, and different e mail accounts from spam, viruses, and different malicious content material. Set up anti-spam filters in your digital gadgets (e.g., computer systems, telephones) that entry the web by means of wi-fi or wired networks.
Think about putting in a virus safety program on digital gadgets along with utilizing antispam filters. You may customise such anti-virus packages based mostly on particular e mail safety protocols for superior safety.
3. Use 2-factor authentication
When customers rely solely on password safety to safe their e mail, 2-factor authentication gives one other layer of safety. This consists of utilizing a secondary issue, corresponding to a code despatched to their smartphone to achieve entry.
By requiring each components for somebody to log into their account, they’re considerably much less possible to have the ability to compromise it with out first realizing the password and code. As well as, entrepreneurs can leverage two-factor authentication to make sure customers with the proper privileges for knowledge entry obtain particular content material.
4. Replace the gadgets you employ to log in
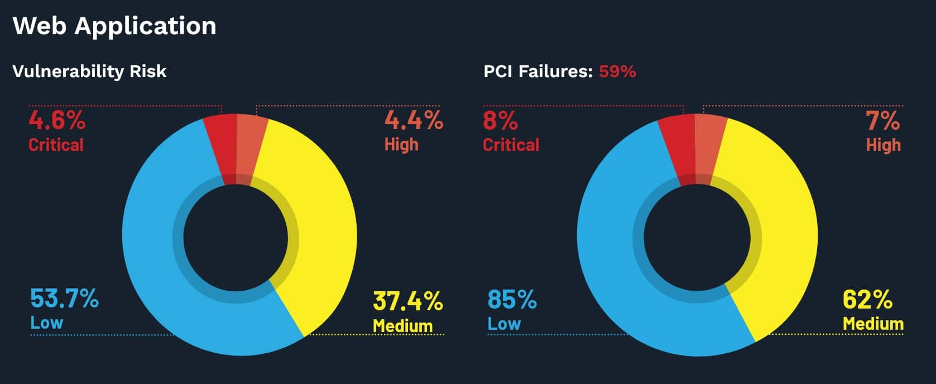
Edgescan’s 2022 Vulnerabilities Report signifies that one in ten net utility vulnerabilities is on the crucial danger degree. It makes safety updates very important for organizations. For instance, e mail advertising and marketing requires communication at a multi-level.
Entrepreneurs goal a number of accounts at any time for advertising and marketing functions, so updating your gadget for safety patches is important. In case your gadgets should not have safety patches put in, net app vulnerabilities can have an effect on gadgets and all the e-mail communications that occur by means of them.
5. Solely use trusted Wi-Fi networks
Wi-Fi assaults are a few of the commonest as a consequence of connections on untrusted networks. As an e mail marketer, you have to guarantee a safe connection earlier than speaking with prospects.
Hackers can leverage connections on untrusted networks to entry e mail content material by means of MITM. Subsequently, one of the best method is to make use of trusted Wi-Fi networks and guarantee safe e mail communications.
6. E-mail authentication requirements
E-mail authentication requirements can assist organizations make sure that all their emails are acquired and processed accurately. Moreover, requirements can assist shield towards malicious actors who might attempt to ship faux or unauthorized emails by spoofing the sender’s handle or id.
E-mail authentication requirements are protocols that permit licensed e mail customers to confirm the authenticity of messages. A few of the hottest requirements embrace Easy Mail Switch Protocol (SMTP) e mail verification, Area-based Message Authentication, Reporting and Conformance (DMARC), and Area Keys Identification Mail (DKIM).
- SMTP e mail verification permits the sender of an e mail message to show that they’re legit by requiring them to supply a legitimate SMTP-verified account.
- DKIM is an e mail safety protocol used to confirm the authenticity of emails by including DKIM-signed messages to an e mail’s header. By verifying their authenticity, recipients can make sure that the messages they obtain are from authoritative sources and haven’t been tampered with in any means.
Whereas SMTP and DKIM give attention to securing the accounts or signed messages, DMARC is a extra complete commonplace that allows you to implement e mail safety insurance policies.
7. Think about DMARC
DMARC is an e mail safety protocol that helps to guard e mail site visitors from being spoofed or hijacked. When customers ship emails, DMARC checks the sender’s area towards no matter checklist of blacklisted domains they’ve configured.
If there’s a match, it means somebody has tried to log in because the recipient and will learn their emails with out information. As well as, this safety can assist to forestall private info corresponding to addresses, checking account numbers, and bank card particulars from being stolen in transit by rogue staff or hackers.
It’s important to maintain your DMARC settings up-to-date, so you realize if any modifications have been made to your blacklisting standards. Moreover, it is best to repeatedly monitor your spam folder for suspicious messages associated to cybercrime actions.
8. At all times examine emails earlier than clicking something
Probably the greatest practices to observe is to make sure that the e-mail you click on on is from a trusted supply. Emails that appear like they is perhaps swindles can infect your laptop with adware or different malicious software program.
At all times concentrate on who’s sending you emails and what they’re asking for. Some frequent e mail frauds embrace phishing schemes, the place criminals trick folks into revealing private info corresponding to checking account numbers or passwords. One other crucial e mail greatest observe is to make use of a good browser extension or software program program.
Practice your clients and staff to search for the next indicators that it is perhaps a rip-off:
- The e-mail sender asks for private info corresponding to checking account numbers or passwords
- The e-mail incorporates a request for cash on behalf of somebody throughout the group
- The e-mail appears faux or has a distinct sample than the official message
- E-mail ID appears faux or has an analogous identify to official e mail addresses.
9. Perform routine inside checks
Routine checks are important to make sure that e mail communications stay safe. A single interplay can result in antagonistic results in your marketing campaign. So, listed below are some ideas that you may observe,
- Examine e mail addresses and account passwords are safe.
- Monitor e mail supply experiences to make sure that all emails attain their supposed recipients.
- Deploy efficient spam prevention measures like blocklisting or permitting itemizing for mail senders, establishing antispam filters, and checking for malicious content material.
- Examine the safety of third-party companies that observe your e mail advertising and marketing campaigns.
- Guarantee your e mail safety coverage is updated, together with spam definitions and knowledge entry restrictions.
10. Safe the e-mail gateway and create backups of crucial information
Entrepreneurs are allowed to test despatched emails and thus safety is preserved. A number of safety layers and authentication course of binds every e mail. As well as, you possibly can leverage cloud-based instruments to implement a safe e mail gateway.
Nevertheless, selecting one of the best software to make use of to your e mail safety will depend upon the server sort, corresponding to Home windows Alternate Server. Additional, you have to create a backup of delicate info and information to keep away from knowledge loss if there’s a cyberattack.
11. Create consciousness
Securing your e mail advertising and marketing campaigns require intensive training not only for entrepreneurs but in addition for patrons. Practice your staff and educate clients about e mail scams by means of webinars, blogs, FAQs, movies, and many others.
Some steps to observe for higher e mail safety consciousness are,
- Use a disclaimer on the finish of emails about completely different scams that attackers can use.
- Leverage social media posts for higher buyer consciousness of e mail safety protocols
- Publish FAQs in your net pages for consumer training.
Conclusion
E-mail advertising and marketing is important for a lot of companies as a consequence of higher ROI and conversions. Nevertheless, if you happen to can’t hold e mail advertising and marketing safe, it might probably trigger huge mistrust amongst clients. One of the best ways is to have correct e mail safety protocols and benefit requirements to make sure safe buyer communication.
We’ve got mentioned many various kinds of e mail safety greatest practices. Once more, which one to decide on depends upon the particular necessities of your marketing campaign.
Source link