Scorpion says: “Recover from right here!” Be careful for emails from the crypto trade CoinPayments. Hackers are operating a brand new “Mortal Kombat” ransomware marketing campaign. The attackers disguise the phishing electronic mail attachment to appear to be cost transactions. Nevertheless, when opened, the payload routinely downloads both ransomware or a crypto-wallet skimmer. So it is a bit like a one-two uppercut. TOASTY!
Safety researchers from Cisco’s Talos cybersecurity crew have tracked a brand new ransomware marketing campaign that makes use of photos from Mortal Kombat in its ransom notes. The assaults began showing in December and indiscriminately goal people, small companies, and enormous firms.
As soon as contaminated, the affected laptop shows a Mortal Kombat 11 wallpaper connected to a notice instructing the sufferer to contact the attackers by way of an prompt messaging app referred to as qTox that anybody can download from GitHub. The attackers will then negotiate a worth to be paid in Bitcoin.
The assault vector is phishing emails made to appear to be they’re from the crypto buying and selling platform CoinPayments. The emails declare that the consumer’s cost has “timed out.” An attachment carries the payload in a zipped file with a reputation that appears like a CoinPayments transaction quantity. When opened, it downloads the Mortal Kombat ransomware.
The ransomware will encrypt all information on the sufferer’s PC, together with these within the trash bin and digital machine information. It additionally corrupts Home windows Explorer, deletes folders and information from the startup menu, and disables the Run command. Nevertheless, it would not show any wiper capabilities or erase quantity shadow copies within the laptop.
Talos notes that the e-mail attachment might alternatively obtain Laplas Clipper. This malware displays the pc’s clipboard for cryptocurrency pockets addresses. If it finds one, it sends it to the attacker’s server, the place a “Clipper bot” creates a “lookalike” handle owned by the hacker after which replaces the clipboard entry. Customers then unknowingly switch funds into the hacker’s pockets as an alternative of their very own.
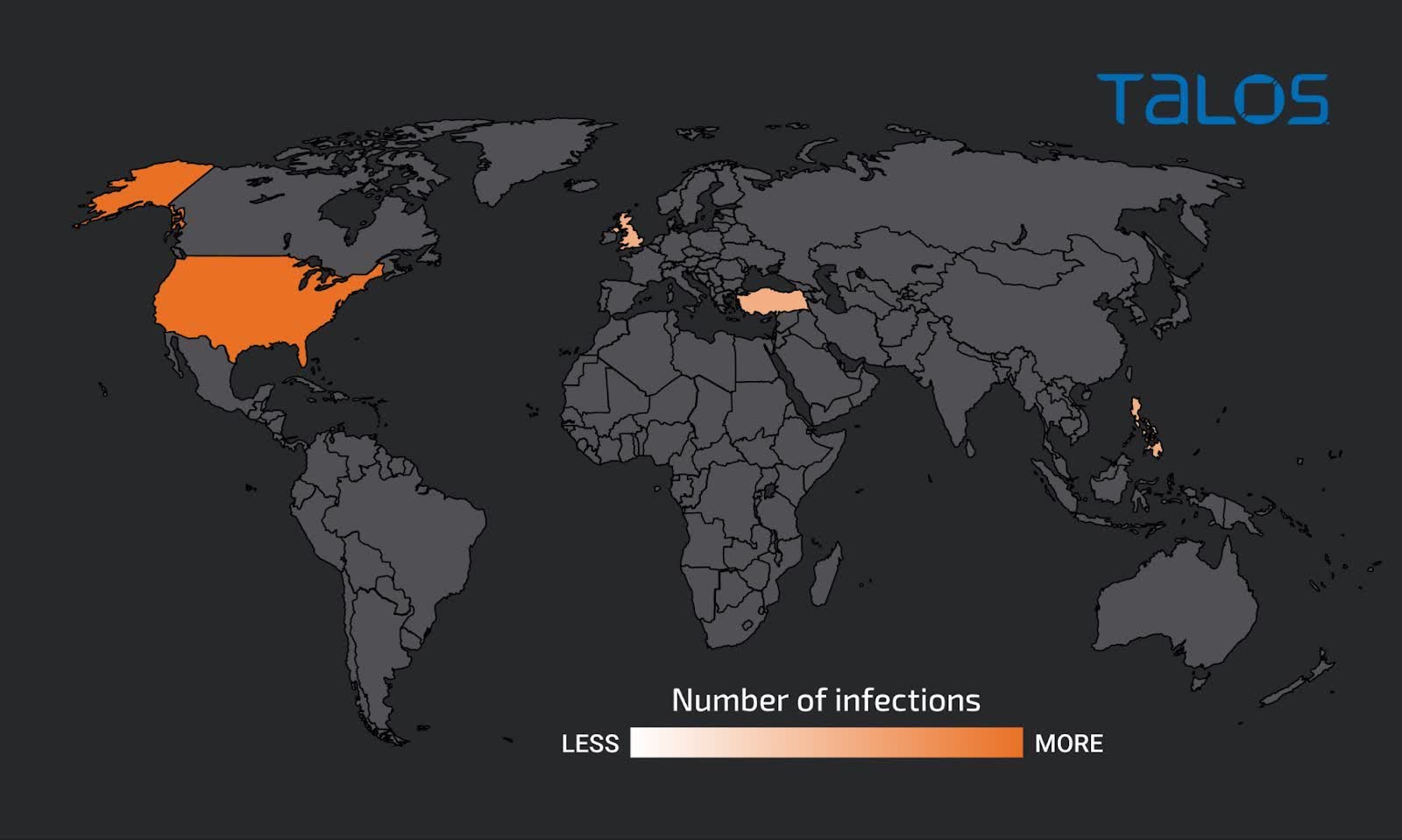
Talos says that though the Mortal Kombat ransomware is new, it seems to be a Xorist variant. Xorist dates again to a minimum of 2010. The researchers tracked assaults, and most appear confined to the USA, with a lightweight scattering of victims in England, Turkey, and the Philippines.
As at all times, the most effective mitigation for ransomware assaults is to stay vigilant and suspicious of random emails from companies you employ. Be careful for attachments or requests on your credentials. Firms not often ship clients information or ask for usernames or passwords.
Source link


