Facepalm: Meta lately applied a centralized login system to make it simpler for Instagram, Fb, and Meta (VR) customers to handle their accounts. Sadly, in establishing the 2FA system, engineers missed a obvious failure relating to try limitation.
A freshman safety researcher named Gtm Mänôz noticed the bug in July 2022. Whereas searching for his first bug bounty to current at BountyCon 2022, Mänôz began taking part in round with the Meta Accounts Center interface, which manages all Meta accounts, including related performance as Google’s one-stop login for its numerous companies (YouTube, Gmail, Docs, and many others).
He famous that the web page allowed customers to affiliate a telephone quantity with their accounts when linking them. Customers merely enter their telephone quantity after which the six-digit 2FA code the system sends them. Nonetheless, Mänôz found that if the unsuitable code is entered, the Account Heart simply asks the person to reinput it as a substitute of sending a brand new code.
Moreover, there was no restrict on what number of failed makes an attempt one might enter into the verification field. This oversight allowed Mänôz to brute power the 2FA on his personal account to affiliate his telephone quantity with one other Fb profile. The one warning comes after the telephone quantity is stolen in an e-mail from Meta to the sufferer informing them that it has been linked to a different person’s account.
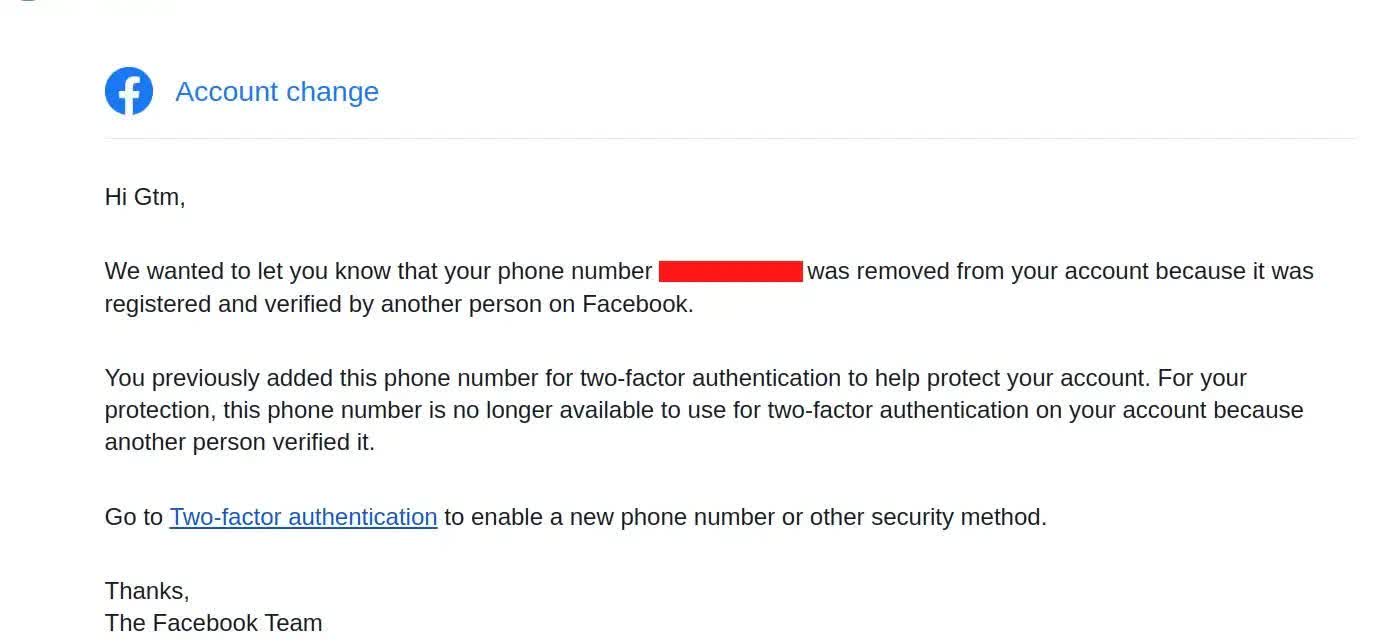
Whereas the harmfulness of this exploit is principally restricted to a bothersome re-establishing of the proprietor’s telephone quantity, it successfully disables 2FA on the sufferer’s account, albeit quickly. Till the goal takes motion, they’re open to password phishing assaults.
“Principally, the very best impression right here was revoking anybody’s SMS-based 2FA simply realizing the telephone quantity,” Mänôz advised TechCrunch.
Mänôz notified Meta of the bug in September, and it patched the vulnerability instantly. A spokesperson mentioned that when Mänôz discovered the issue, the Meta Accounts Heart was nonetheless in beta and solely accessible to a small variety of customers. The consultant additionally famous that Meta’s investigation revealed no spikes within the utilization of that characteristic, indicating that hackers hadn’t exploited it.
Regardless of the comparatively low-treat of the glitch, Meta awarded Mänôz a $27,200 bug bounty. Not too shabby for his first bug hunt.
Meta has stumbled a couple of instances within the final couple of years relating to the login options of its numerous accounts. In 2021, it precipitated a light panic when it logged everybody out of Fb when reconfiguring the web site. Final yr, it purposefully locked many customers out of their accounts for not enabling “Fb Shield” by a deadline set by an official Meta e-mail that seemed suspiciously like a phishing rip-off.
Source link


