A newly detailed form of Android banking malware has been found to be targeting 56 different European banks.
Discovered by researchers at ThreatFabric and revealed today, the banking trojan has been dubbed “Xenomorph” because it has its roots in a previous form of Android malware called Alien. The Alien mobile malware was first detected in January 2020 and was a fork of the Cerberus Android malware.
The Xenomorph name makes sense since it’s the third-generation variant of the original Cerberus malware. While having fallen out of favor with hackers, Cerberus once made headlines, such as in February 2020, for compromising Google LLC Authenticator.
Sadly but not surprisingly, Xenomorph has been found in applications on the Google Play Store. The ThreatFabric researchers note that while Google has seemingly taken some action to reduce the number of malicious applications on its store, these efforts are not enough to stop criminals from reaching the store.
As is typical with Android malware distribution, Xenomorph is hidden in what appear to be legitimate applications. One such application was “Fast Cleaner.” The app was pitched as speeding up a device by removing unused clutter and removing battery optimization blocks. Before being removed from Google Play, the app had more than 50,000 installations.
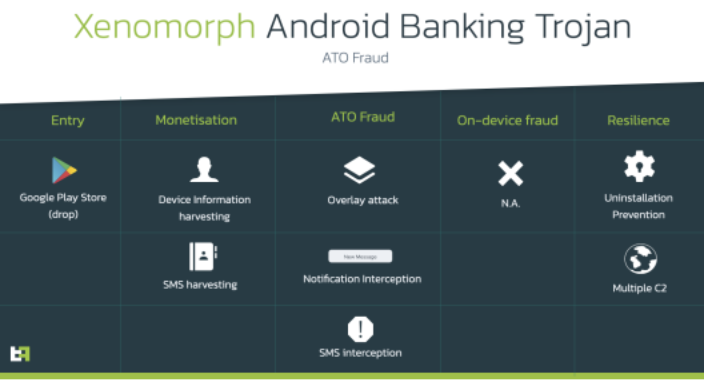
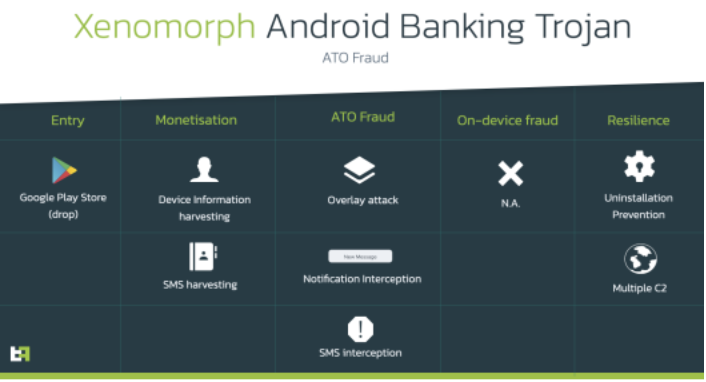
Xenomorph uses an overlay attack to steal credentials. In an overlay attack, a malicious app opens and activates a window over a legitimate program. This layer fully replicates the target product interface, with the user being none the wiser. Given that Xenomorph targets 56 European banks, a user opening their banking app would be presented with a screen that appeared to be their banking app but was actually a fake overlay of their login screen.
To make matters worse, Xenomorph also intercepts SMS messages and two-factor authentication programs to intercept and gain access to victims’ bank accounts.
The researchers add that Xenomorph appears to be in its early stages of development — in their words, its “infancy” stage. That’s based on code analysis that many commands are present in the malware that have not yet been implemented.
“The surfacing of Xenomorph shows, once again, that threat actors are focusing their attention on landing applications on official markets,” the ThreatFabric researchers conclude. “This is also a signal that the underground market for droppers and distribution actors has increased its activity.”
Image: ThreatFabric
Show your support for our mission by joining our Cube Club and Cube Event Community of experts. Join the community that includes Amazon Web Services and Amazon.com CEO Andy Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger and many more luminaries and experts.

Source link