E-mail remains to be one of many strongest channels for advertising and marketing and enterprise progress. The Wall Road Journal calls electronic mail “the one guaranteed-delivery possibility the web has left,”.
Promoting is dear. Social attain might change in a single day. web optimization outcomes can rise or fall with out warning. However an electronic mail checklist is one thing you personal. It lets you management how and if you talk.
That’s why constructing a secure electronic mail acquisition funnel issues. Dangerous or faux emails harm you at a number of ranges. They will harm deliverability. They will decrease sender repute. And sure, they may scale back income. A clear checklist begins on the entry level, when a consumer first submits their electronic mail.
On this information, we clarify the 7 easy steps to seize solely legitimate, actual, and safe-to-send electronic mail addresses. Observe them correctly and shortly you’ll have a listing that connects, engages, and buys from you.
Come, let’s begin constructing progress!
What’s a secure electronic mail acquisition funnel?
A secure electronic mail acquisition funnel is a channel from the place you gather deliverable, consented electronic mail addresses.
Within the definition of a secure electronic mail acquisition channel above, discover two phrases: deliverable and consented. Right here’s what it means:
- Deliverable: The e-mail addresses ought to be safe-to-send. In different phrases, if you happen to ship emails to these addresses, your emails will most certainly land within the inbox. The likelihood that they may bounce is nearly zero. It’s as a result of the real-time electronic mail verification answer in your acquisition funnel validates each single electronic mail earlier than including it to your checklist.
- Consented: This implies the proprietor of the e-mail deal with has offered you clear consent to ship them emails. It additionally comes with an implicit belief that you simply gained’t abuse, share, or promote these emails.
Why unhealthy emails enter your system within the first place
Dangerous emails enter your system by mistake in addition to by design. Folks commit typos. So, the e-mail that ought to have been, as an illustration, robert@electronic mail finally ends up as rpbert@electronic mail in your electronic mail checklist.
In different instances, customers deliberately enter a faux or disposable deal with to entry gated content material. That’s executed largely as a result of they believe the group may resell or abuse their electronic mail.
Both manner, you’ll see a variety of invalid or disposable, low-quality electronic mail addresses in your checklist.
Over time, such electronic mail addresses scale back checklist high quality, decrease engagement, and harm your sender repute.
How an automatic filtering funnel solves this
A secure electronic mail acquisition funnel provides verification checkpoints at each stage. In case of a typo, the system will counsel an accurate different each time possible (‘Did you imply [email protected] as an alternative of [email protected]?’).
This real-time electronic mail verification system will reject disposable emails. It will possibly additionally flash a message, “Please submit a legitimate electronic mail deal with.”. The system will flag dangerous electronic mail addresses for assessment. In brief, automation does the heavy lifting. Subsequently, solely clear, certified emails enter your electronic mail checklist.
Why the secure channel issues
Emails can increase income and assist drive progress.
In the event you aren’t utilizing emails, you might be ignoring a high-ROI channel. Even not monitoring the e-mail checklist high quality hurts.
Organizations lose an estimated 15% of their annual income (a median of about $12.9M) on account of poor high quality of contacts.
Now you recognize why a secure electronic mail list-building channel is so essential.
Listed here are the 7 steps to construct an electronic mail acquisition channel that lets you gather legitimate, related, addresses:
Step 1: Begin with related, high-quality visitors sources
Your electronic mail checklist high quality is barely as sturdy as your visitors supply. Site visitors supply not related? You should still gather legitimate emails, however conversion charges keep low.
So step one is to enhance the place your leads come from. A high-quality supply improves your checklist, reduces dangerous addresses, and brings in electronic mail contacts which might be extra related to your small business.
Channels that produce clear information
Natural channels often ship one of the best information high quality.
Genuinely customers come by way of:
- web site sign-ups,
- content material downloads,
- webinars,
- product trials, and
- referral packages
These guests make investments time to study your product, which lowers the possibility of pretend or disposable emails.
In the event you’re planning to make use of paid channels, listed below are some choices to gather dependable submissions:
- paid channels, constructed with considerate concentrating on,
- area of interest search adverts,
- intent-led platforms, and
- retargeting campaigns
Channels that often generate dangerous emails
Irrelevant visitors usually results in dangerous electronic mail submissions. For instance, if you happen to promote industrial fasteners, selling content material on pages about meals recipes will deliver poor-quality leads.
Listed here are among the possible channels that deliver low-quality emails:
- Broad giveaways,
- contests,
- coupon-based campaigns,
- influencer broad shoutouts, and
- poorly focused adverts that appeal to customers who need the reward, not the product
Such customers usually tend to enter disposable or faux emails. Recognizing these patterns helps entrepreneurs construct the precise verification steps for high-risk visitors.
Step 2: Construct smarter signup and lead seize kinds
Many entrepreneurs see signup kinds as easy assortment instruments. However kinds play a serious function in defending electronic mail information. A wise type reduces friction for real customers and blocks low-quality submissions early. That helps you preserve a clear checklist.
Use real-time electronic mail verification
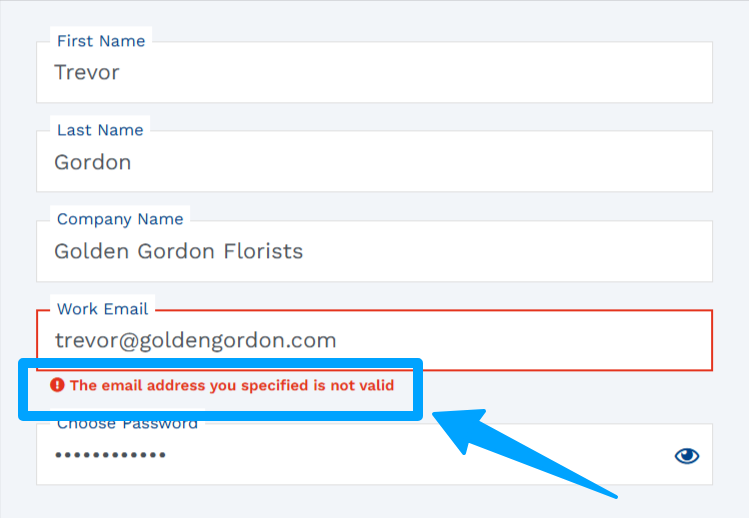
Actual-time verification is your first safeguard. The second a consumer submits an electronic mail, the system checks whether or not it’s legitimate, deliverable, and secure to ship. It’s instantaneous high quality management.
This stops dangerous emails from getting into your ESP and stop subsequent hard-bounce. Solely verified emails will transfer to the subsequent stage.
Add typo detection and suggestion prompts
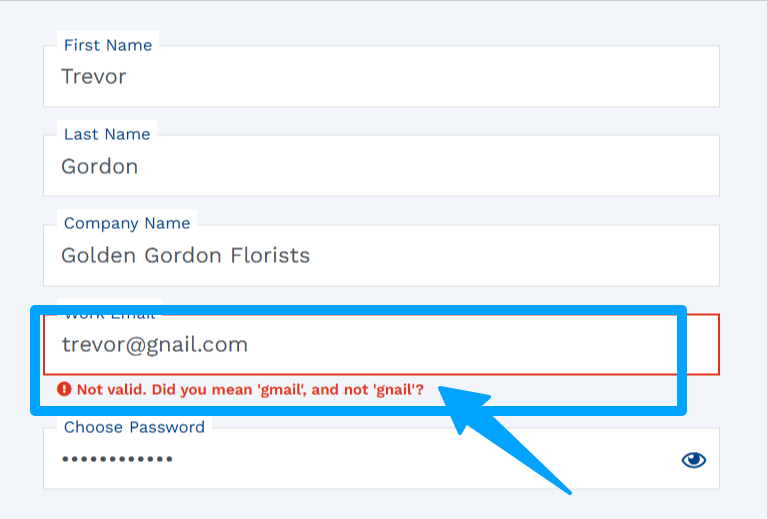
Typos are surprisingly frequent. Somebody varieties gmial as an alternative of gmail, or yaho as an alternative of yahoo. With out intervention, these small errors degrade your checklist over time.
Sensible kinds catch these slip-ups and counsel corrections on the spot. One thing so simple as “Did you ‘gmail’, and never ‘gnail’?” can recuperate a lead that may have in any other case bounced.
Block disposable and momentary emails immediately
Some customers enter throwaway addresses to entry gated content material. Such emails harm engagement and harm segmentation. Your type ought to reject such domains and request a legitimate electronic mail as an alternative.
Types can’t obtain this on their very own. You want the precise real-time email validation tool to fend off the unhealthy high quality of emails out of your type.
Step 3: Have verification at each entry level
Defending your sign-up type is important however not sufficient. It is advisable take note of all different entry factors the place subscribers are more likely to submit their emails.
In case your group is like different organizations, it collects emails from a number of sources. And with a purpose to do that easily and securely, it is advisable mitigate the dangers at each touchpoint.
A single unchecked entry level can introduce tons of of unhealthy addresses into your system. That’s why verification must be energetic wherever emails enter your ecosystem.
Touchdown pages
Touchdown pages are constructed to draw high-intent customers. However will they appeal to bots or bulk submissions? Sure, particularly if the web page is promoted closely.
Including verification right here ensures that each electronic mail is checked earlier than it’s accepted. Whether or not the customer is signing up for a trial, a demo, or a publication, real-time electronic mail verification ensures that solely legitimate and safe-to-send emails get a inexperienced sign.
Lead magnets and gated content material
Do you utilize stories, templates, checklists, and ebooks to deliver giant volumes of leads in a short while? Then you definately in all probability know that they can be magnets for disposable or faux emails.
You need to grant entry to your gated content material solely to customers who’re keen to share their legitimate emails. So have real-time verification in place – that manner, the consumer will nonetheless get the content material however solely after submitting an actual, usable electronic mail deal with. And you are able to do this with out ruining consumer expertise.
Gross sales outreach lists and handbook imports
Gross sales groups usually add emails from occasions, webinars, one-to-one conferences, and so forth. These sources might be riskier than the others, as a result of handbook entries vastly enhance the chance of typos.
Run verification earlier than importing these contacts. Utilizing a strong email checker prevents bounces, protects area repute, and ensures gross sales emails attain actual prospects as an alternative of harming sender credibility.
Step 4: Automate filtering inside your CRM/ESP
As soon as emails enter your CRM or ESP, you’ll want automation to make the e-mail verification system your second line of protection. Guide checks can not scale, particularly when a number of groups add contacts by way of workflows, integrations, or direct imports.
Automated filtering ensures that your database stays clear even when new entries are available from all instructions.
Set guidelines to reject invalid or dangerous emails
Most CRMs and ESPs assist you to create fundamental guidelines or validation checks. These guidelines can routinely block recognized invalid codecs, reject addresses from suspicious domains, and cease submissions that fail verification.
As a substitute of letting problematic information slip by way of and hurt your campaigns later, the CRM quietly prevents it from getting into the system within the first place.
Auto-tag catch-all, function, and low-quality emails
Some emails, though deliverable, require warning. Catch-all domains, role-based addresses (like data@ or assist@), and low-quality sources ought to be tagged the second they enter your CRM.
Tagging helps your advertising and marketing and gross sales groups determine deal with these contacts – whether or not to nurture them gently, validate them once more, or exclude them from campaigns.
Figuring out how to manage the risks of catch-all, disposable, or role addresses is essential to getting extra out of your campaigns even whilst you prune your electronic mail lists.
Set off cleanup workflows
Fashionable platforms like HubSpot and Salesforce permit automated workflows that deal with cleanup behind the scenes. You possibly can routinely re-verify older contacts. Primarily based on the outcomes, you’ll be able to quarantine uncertain emails and discard invalid ones.
These workflows guarantee ongoing information hygiene. You possibly can scale back handbook effort and maintain your sender repute secure, irrespective of how giant your database grows.
Step 5: Section your leads earlier than sending
Completely different campaigns have totally different threat appetites. The character of the marketing campaign performs a big function in deciding whether or not the marketer desires to forged their internet huge or simply play secure. Treating all electronic mail contacts equally in all conditions is the place many manufacturers lose deliverability momentum.
Earlier than you hit “Ship”, you may need to rating and phase your leads in order that the precise message reaches the precise kind of deal with.
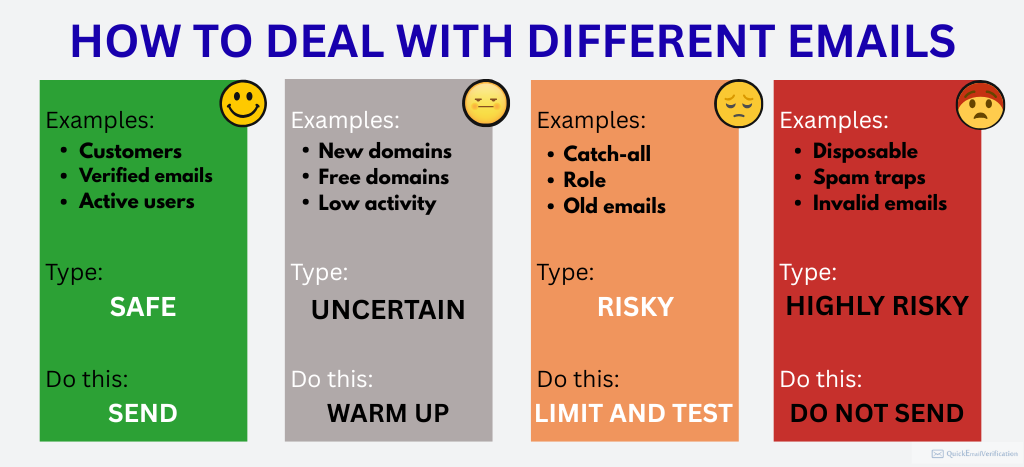
Create threat classes (secure, unsure, dangerous)
Lead scoring doesn’t solely apply to intent; it applies to electronic mail high quality as properly.
Secure leads imply:
- clear and verified electronic mail addresses, and
- energetic and just lately engaged addresses
Unsure leads are:
- catch-all domains,
- older addresses who haven’t been contacted just lately, and
- emails acquired from much less predictable channels
Dangerous leads might embrace:
- function accounts, and
- E-mail addresses entered manually (by typing) and but not verified or contacted
Extremely threat emails embrace:
- electronic mail addresses from disposable domains, and
- addresses beforehand related to arduous bounces
Creating these classes helps you management how aggressively you electronic mail every group, and it reduces the possibilities of sudden deliverability drops.
Coping with emails with several types of dangers
Right here’s a desk that exhibits take care of dangerous emails:
If the variety of emails is greater than 2% of your electronic mail checklist, think about asking them for a double opt-in.
Sort of electronic mail
Really useful motion
Extremely dangerous: Disposable electronic mail
Discard these emails.
Extremely dangerous: Beforehand arduous bounced and no subsequent engagement
Discard these emails.
Dangerous: Beforehand arduous bounced, then had engagement for a short interval, after which you haven’t emailed them for a while
That is the rarest class. Ship one re-engagement electronic mail asking them to substantiate their subscription.
— Discard if that electronic mail bounces
— Suppress if neither engages nor bounces
— Transfer to common checklist in the event that they affirm subscription
Dangerous: Function accounts
Put them in a re-engagement electronic mail sequence, asking them to substantiate their subscription.
Dangerous: Emails entered manually and never verified after that
Step 1: Confirm these electronic mail addresses.
Step 2: Primarily based on the e-mail verification outcomes, discard emails that fall underneath the Extremely Dangerous class or are Invalid emails. For legitimate emails, observe Step 3.
Step 3: Ship them a re-engagement electronic mail asking them to substantiate their subscription.
Unsure leads: Catch-all electronic mail domains
Heat them up. Ship emails slowly after which enhance the frequency and produce them at par with different Secure-to-Ship emails.
Unsure leads: Older addresses with no current contact
Step 1: Confirm these electronic mail addresses.
Step 2: Discard emails that fall underneath the Extremely Dangerous class or are Invalid emails. For legitimate emails, observe step 3.
Step 3: To legitimate emails, ship a re-engagement electronic mail asking them to substantiate their subscription
Secure leads
Proceed sending legit, common emails.
This strategy ensures your strongest campaigns at all times attain your strongest contacts.
Step 6: Run a re-verification layer earlier than campaigns
Folks change jobs, abandon inboxes, change domains, or enroll with momentary addresses that expire with out warning. Subsequently, their earlier emails die.
An estimated 25% emails – one in each 4 -turn invalid yearly.
In actual fact, most estimates place the e-mail decay fee between 20% and 30% yearly. That’s why including a re-verification layer earlier than main campaigns is important.
Why this prevents last-minute bounce points
Re-verification catches addresses which have quietly turned invalid since your final cleanup. With out it, you threat sudden spikes in arduous bounces. That may harm sender repute in a single marketing campaign. ESPs are inclined to interpret surprising bounce surges as an indication of poor checklist administration. Therefore, you’ll possible see decreased inbox placement instantly after.
A easy re-verification move prevents these surprises and protects the goodwill you’ve constructed with mailbox suppliers.
When to re-verify previous or chilly leads
Right here’s handle the standard of emails from outdoors your most important funnel.
Frequently clear the lists you’ve:
- collected from occasions.
- constructed from tradeshow scans,
- mixed from uploaded spreadsheets, or
- generated from information sources outdoors your most important funnel
Earlier than seasonal sends (like Black Friday) or high-volume bulletins, observe a easy step. Go for a contemporary verification sweep to make sure you’re emailing actual, energetic inboxes, and never outdated or dangerous addresses.
Think about re-verification of your checklist in not less than two situations:
- You haven’t despatched a marketing campaign to that checklist prior to now three months.
- You haven’t cleaned the checklist prior to now 60 to 90 days, and your system doesn’t routinely take away bounces from the sending checklist.
Step 7: Monitor your the information well being of your funnel
Think about you’ve a machine that makes paper cups from the paper you feed it. Periodically, you’ll want to wash the machine, verify the dials and knobs, take a look at the wiring, oil some components, … Irrespective of how good the machine is, you gained’t anticipate it to run endlessly, with none want for upkeep or repairs, proper?
That’s just about the identical with electronic mail lists.
You possibly can’t construct a secure electronic mail acquisition funnel as soon as, after which assume that it’s good endlessly and overlook it. Information high quality consistently shifts as visitors sources change, campaigns go dwell, and consumer conduct evolves.
Monitoring your funnel’s well being ensures you catch early warning indicators earlier than they escalate into deliverability issues. Consider it as routine upkeep: small checks that forestall massive breakdowns later.
Bounce fee and grievance traits
Bounce charges are one of many clearest alerts of information high quality. A sudden enhance often signifies that invalid, expired, or poorly captured emails have entered your system.
Monitoring each arduous and smooth bounces helps you determine patterns shortly. Complaints matter simply as a lot. If spam complaints begin to rise (even barely) mailbox suppliers might throttle your inbox placement, and even droop your account, quickly or completely.
Complaints usually spike when low-interest or low-quality contacts slip into campaigns. Monitoring these two metrics collectively offers you a dependable view of how engaged your checklist actually is.
Figuring out acquisition sources creating unhealthy information
Not all visitors sources carry out equally. Some channels constantly ship engaged, high-quality subscribers, whereas others quietly pollute your electronic mail checklist. So that you need to assessment every acquisition pathway, i.e., touchdown pages, social adverts, webinars, lead magnets, and occasion imports.
Discover which channels produce greater bounce charges or decrease engagement. When a supply repeatedly contributes unhealthy information, tighten verification on that channel, refine the viewers concentrating on, or take away it solely. Over time, this source-level perception shapes a stronger, extra predictable electronic mail acquisition ecosystem.
Remaining takeaway: Clear leads = secure sending
An efficient electronic mail marketing campaign doesn’t begin if you hit “Ship.” It begins a lot earlier – in the meanwhile a lead enters your system. It is advisable shield each entry level. You need to make it possible for each type is wise and confirm each contact. That’s the place you’re taking a very powerful step of bettering your electronic mail deliverability.
When your acquisition course of constantly filters out unhealthy information, your campaigns attain actual folks. Then, your engagement rises naturally, and your area stays protected. In electronic mail advertising and marketing, progress is easy: shield the highest of your funnel, and the bottom-line will deal with itself.
Source link



